What is DSPM and how is it different from DAM?
Introduction
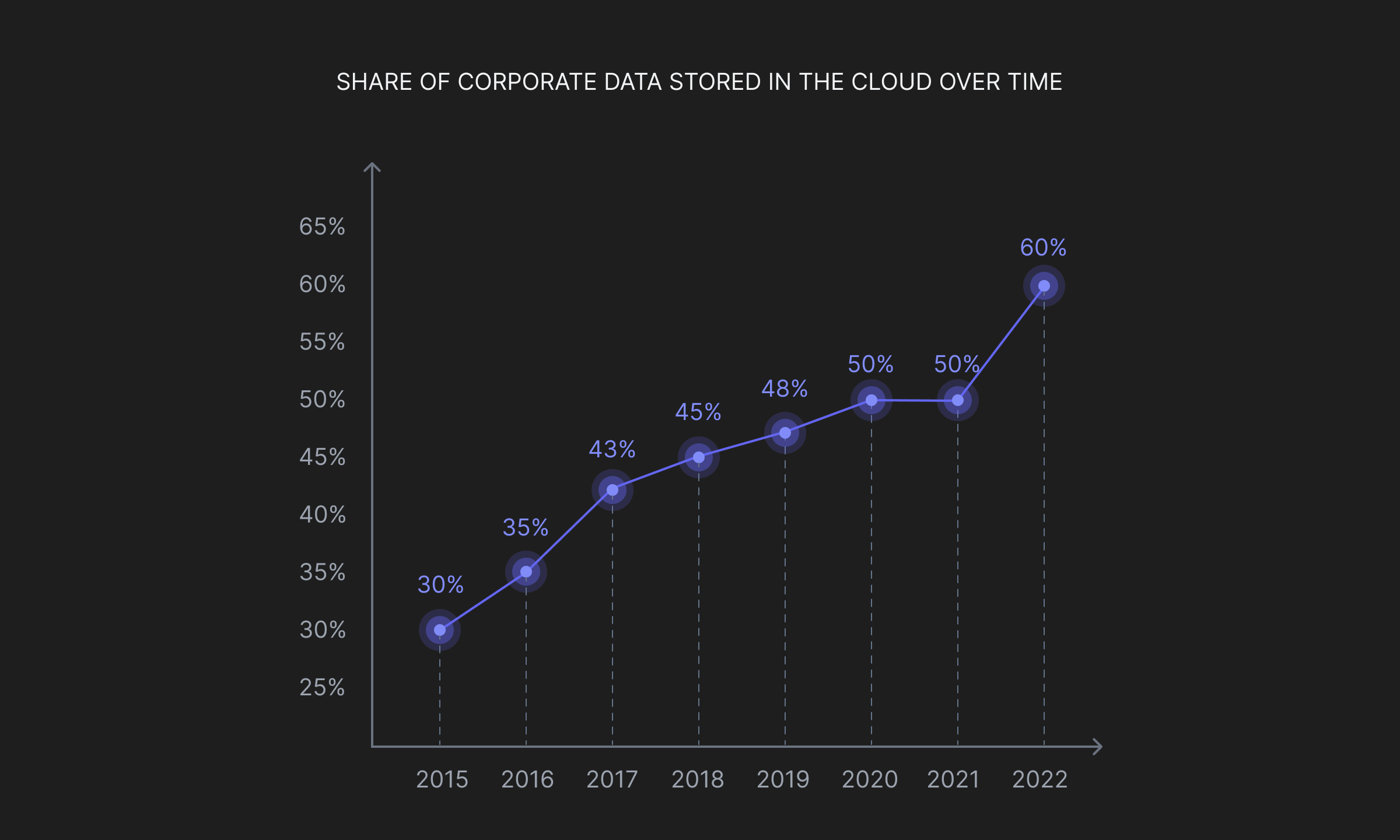
In a span of just seven years, corporate data on the cloud has more than doubled. From 30% in 2015, organizations now depend on the cloud for over 60% of their storage requirements.
The steady and steep adoption of the cloud is a widely recognized trend. However, what is often overlooked are the security concerns that come with it. While cloud service providers invest heavily in physical security of their data centers, strong encryption, and robust access control, 93% of businesses and executives identify cloud security as their critical concern. Specific concerns vary from data leakage, improper visibility into file uploads/downloads, DLP policy violations, and external sharing over the cloud.
Data Security Posture Management for Multi-cloud organizations
DSPM is a comprehensive framework of static practices, designed to bolster an organization's security posture. These practices aim to mitigate potential vulnerabilities within the organization's infrastructure, track the movement and storage of sensitive data, categorize data based on its importance, and trigger alerts to the security team when any anomalous activity is detected.
Data Security Posture Management is best understood by when it comes to use -
Discovering Sensitive Data
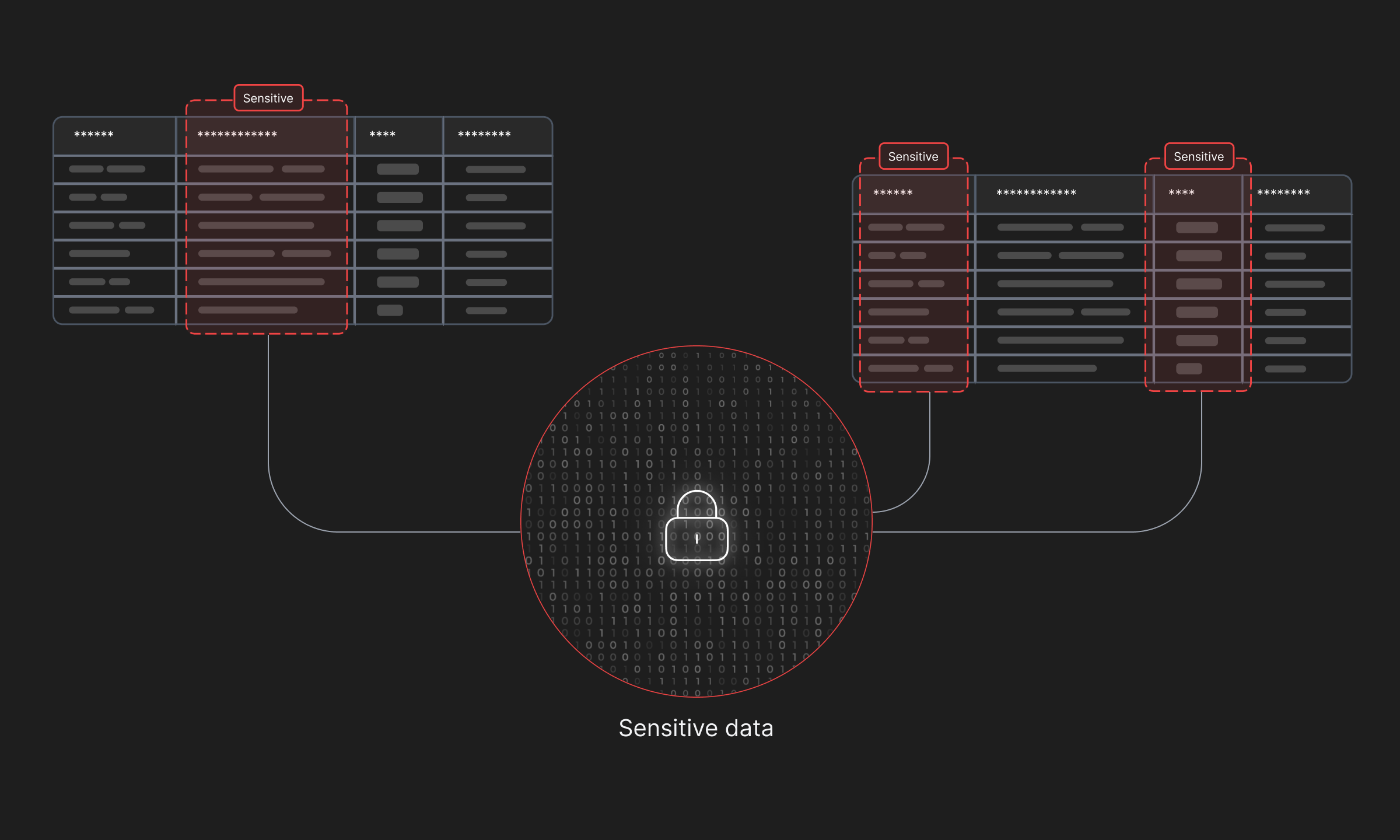
Sensitive data is the root cause of all data breaches, and monitoring where it is stored is of utmost importance. However, for organizations operating with multiple databases and/or handling large amounts of data, tracking it isn’t the easiest of tasks. DSPM tools create automations and can algorithmically recognize fields containing sensitive data based on pre-defined rules, patterns and even probabilities.
Classification of Labelled Data
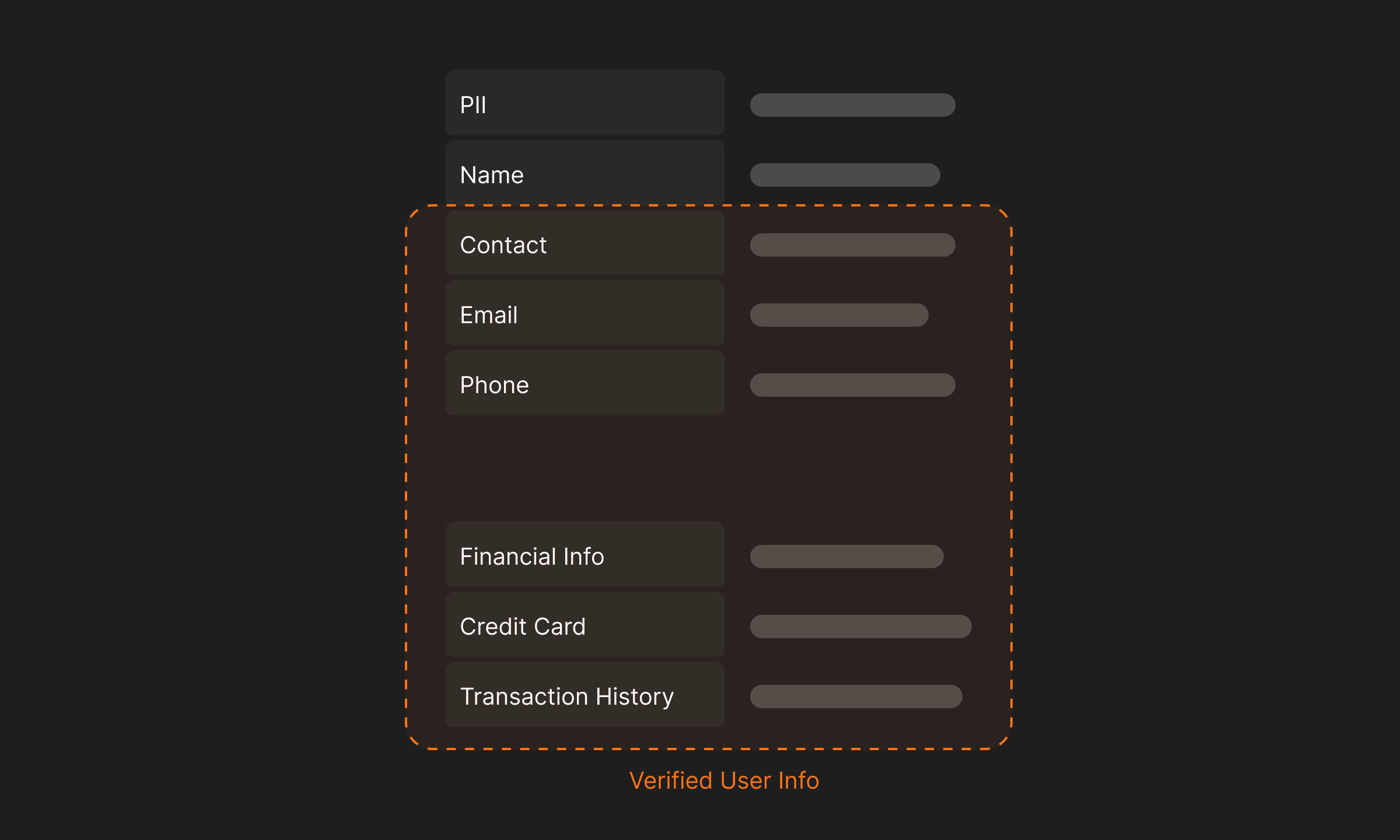
While all sensitive data is at risk, certain information can cause greater damage if leaked. For instance, Personally Identifiable Information (PII) of verified users on a social media platform like Twitter (now X.com) can be used to target individuals with higher disposable income compared to regular Twitter users. This information could be misused to direct advertisements, which is one of the less exploitative ways such data can be utilized.
By employing security tools, an organization can effectively distinguish between different types of sensitive data and design incident response pipelines based on the significance and severity of the data breach. Employing DSPM in this scenario not only helps maintain a stronger security posture, but also optimizes resource utilization, thereby keeping costs low without compromising on security.
Managing Risk
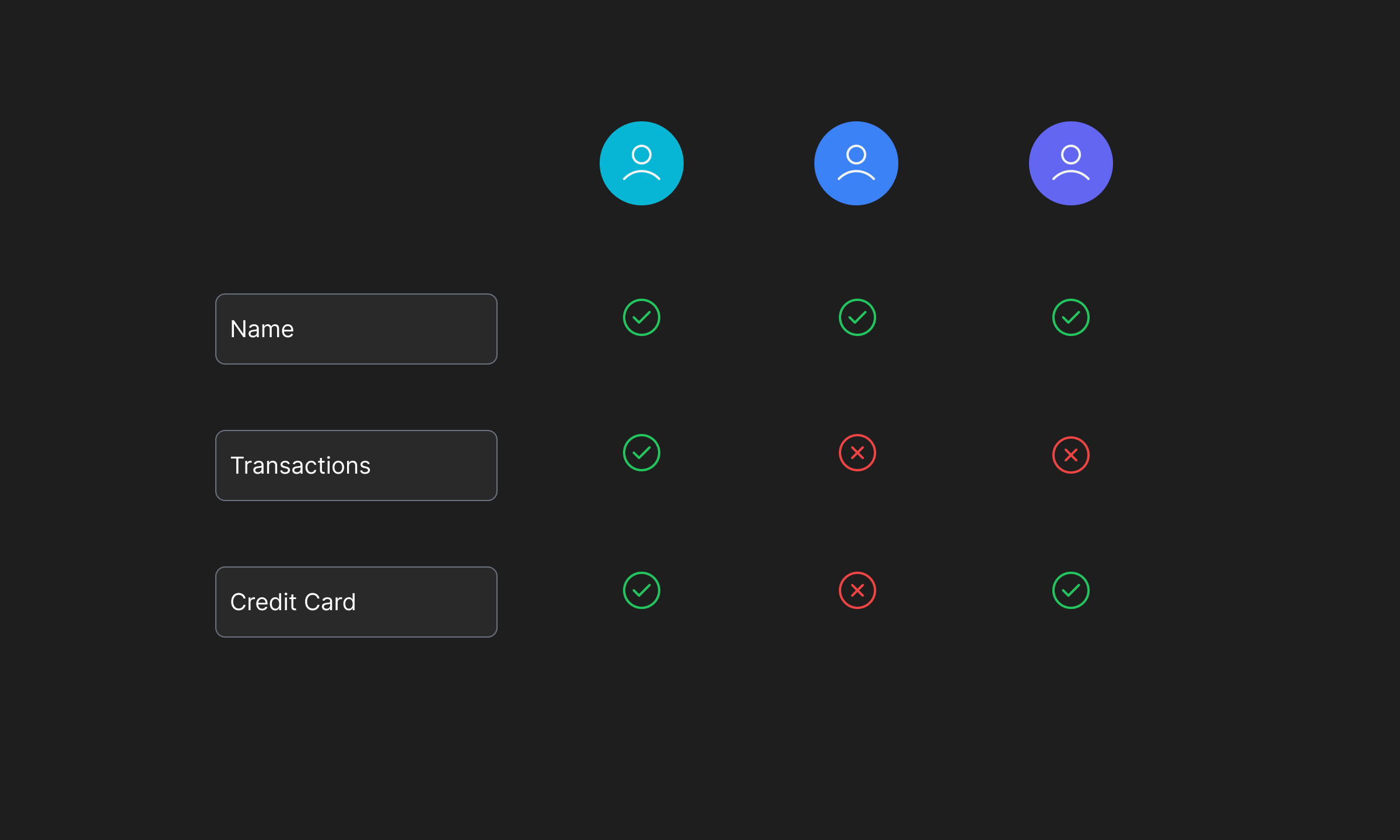
Proper data landscaping and labelling itself creates a stronger posture for your organization as it ensures, at all times, that the sensitive data is monitored and any mis-use such as copying, exporting, deleting, or altering without proper permissions is prohibited and in the worst case; duly caught and reported.
Further analysing the data and its flow to identify vulnerabilities and to achieve a better security posture helps manage risks by allowing security teams to employ granular access controls, encrypt data where necessary and monitor all activity over time for automated threat recognition using heuristics and/or trained Machine Learning models.
Assessing Security Posture
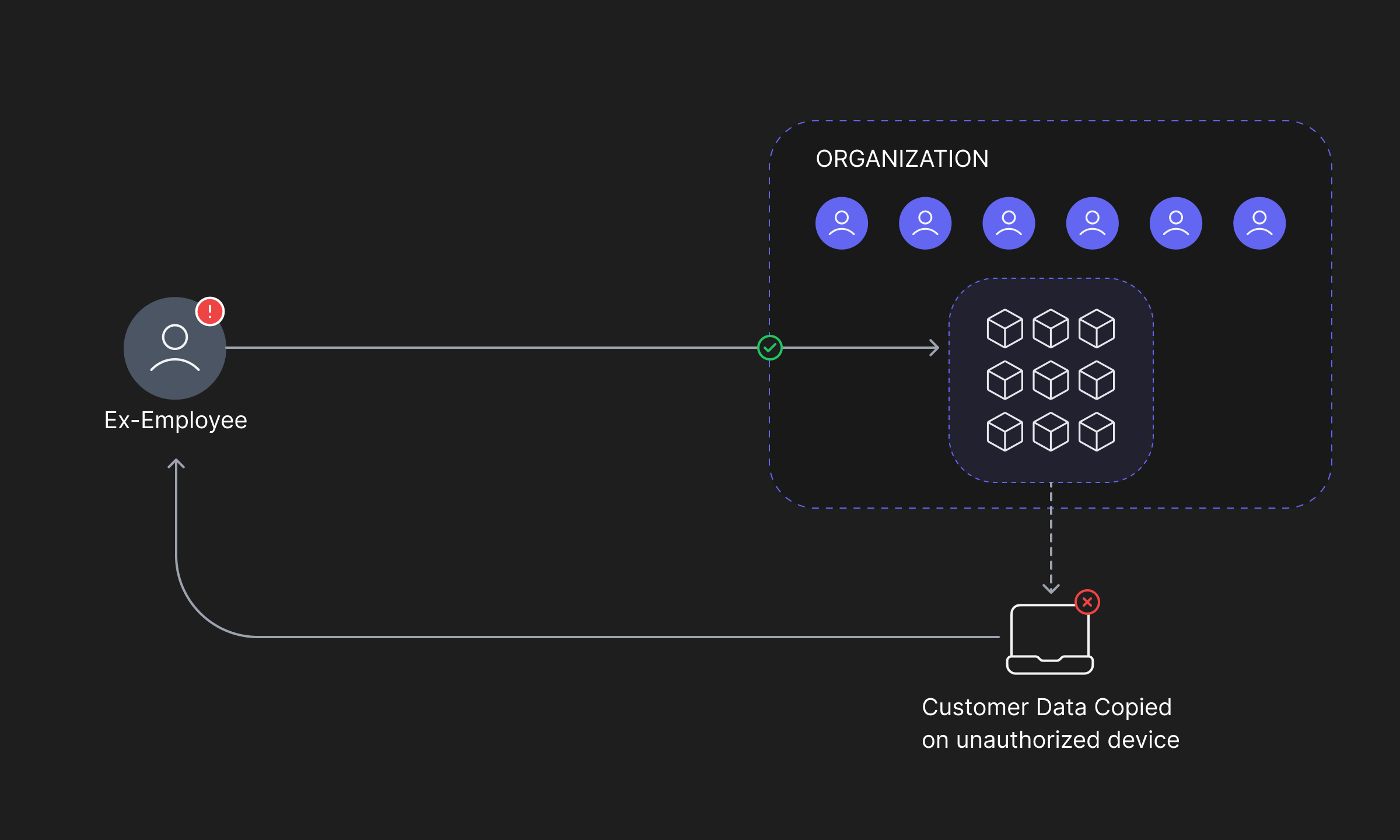
DSPM serves as a high-level tool for ensuring data security within an organization. It helps security teams identify vulnerabilities in the infrastructure's resources, such as replicated data, unnecessary privileges, or unauthorized activity. By doing so, it enables the development of stronger security measures and the faster resolution of these vulnerabilities, ultimately improving overall security posture.
Furthermore, continuous DSPM allows for the identification of new threats and attack vectors as they evolve, ensuring ongoing protection of the infrastructure.
Limitations of DSPM
Constantly analysing and improving the security posture is critical for a Data First organization of the future. However, legacy DSPM tools are limited by their capabilities in two aspects -
Lack of Real-time monitoring
One major shortcoming of static threat analysis (DSPM) is the time it takes to recognize malicious activity and respond to it. Data exfiltration can be an ongoing effort by malicious attackers lasting months or even years, but more often it only takes minutes to transfer a large amount of data from a database to an external resource. Therefore, an average breach discovery time of 110 days suggests a flaw in the foundations of data security. To be able to detect incidents within minutes, active monitoring of all activity in the organization's infrastructure is necessary. However, it is an expensive operation to monitor every activity and consecutively an engineering challenge.
Lack of insights into the malicious activity itself
To achieve faster incident response, it is important to have effective monitoring practices that can quickly identify what changes were made, how they were accessed, and by whom. Current DSPM tools and practices primarily focus on high-level statistics, which require an incident to occur before threat models can detect and report it. However, in the real world, organizations cannot afford to be passive while their valuable information is at risk.
In order to address this, it becomes necessary to define, monitor, and manage permissions at a granular level. This ensures that security teams' resources are optimally utilized while also safeguarding valuable information.
Database Activity Monitoring
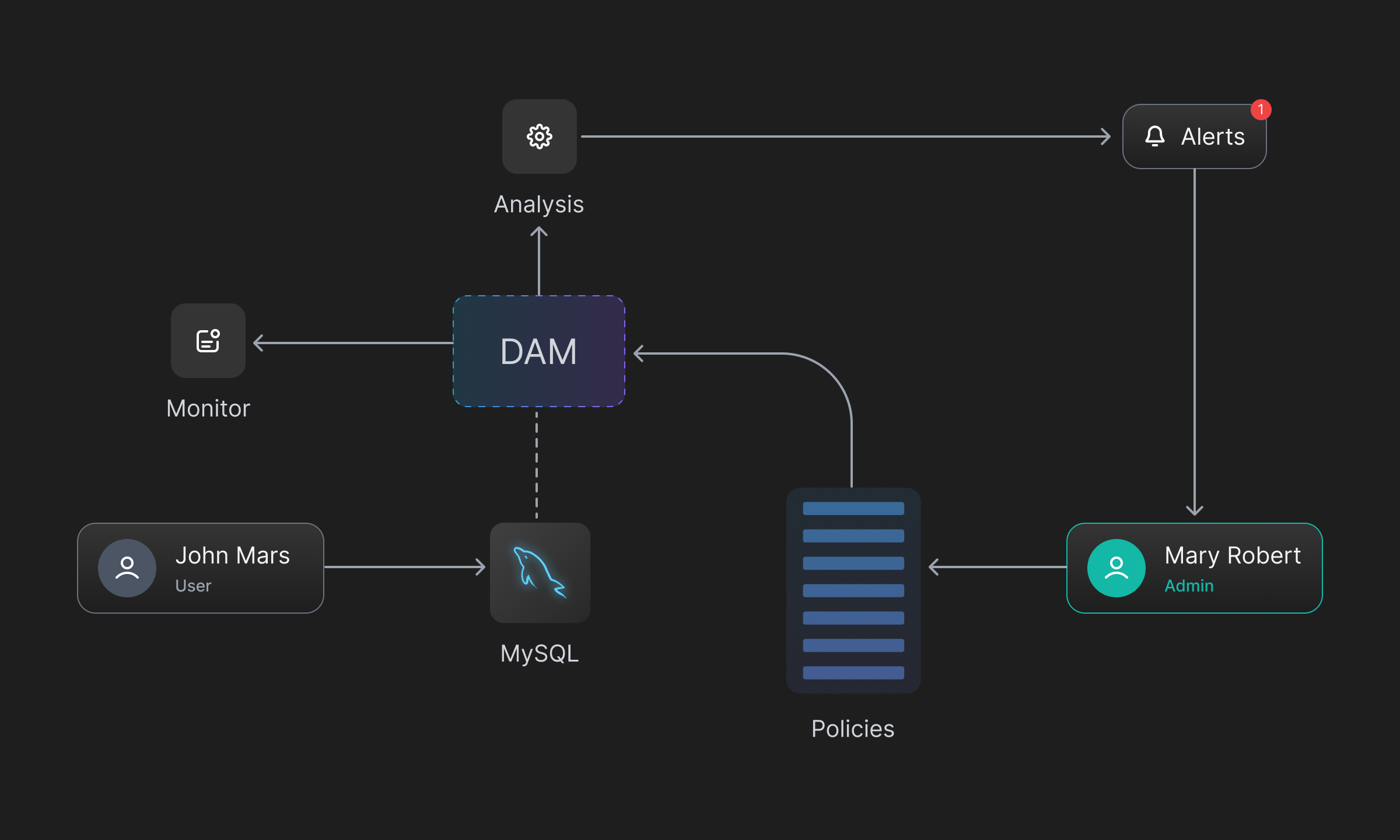
Database Activity Monitoring (DAM) is an architecture that efficiently captures all activity in an organization's resources and provides near real-time availability without significantly impacting the end users' experience. The activity is captured independently of the DBMS native audits and logs providing increased flexibility to design policies and define stronger access controls.
Apart from being near real time, some essential key features of DAM include -
Auditing and Monitoring Database Activity
DAM effectively examines any access or changes made to records, to determine effectiveness of the security controls, and ensures continued compliance with established system policies. Not just that, it runs threat models and detects any potential or ongoing data breaches and also suggests effective counter measures.
A separate store for database activity
Monitoring all database activity isn’t easy. To effectively monitor all system resources, a tool or service needs to perform additional reads and writes every time someone (authorized or not) access a resource and performs an action. Obviously, this is very costly and can reflect poorly on the end users’ experience who expect a seamless response to their database requests.
DAM efficiently saves these actions in a separate store from the DBMS native audits and logs. It accomplishes this by listening to user access, data changes, or updates. With this comes increased flexibility to run sophisticated threat models for vulnerability management and early intrusion prevention, without affecting system performance.
Flexibility to design and define policies
DAM allows administrators the flexibility to define policies and triggers, in a very intuitive way. These policies can be configured to prevent the modification of critical data, detect and prevent access to classified information, and manage various types of changes in the database. The system also allows risk-based conditional access, which controls access based on how susceptible the system is to being attacked by the user. This depends on many factors, including the device being used to access the information, the user accessing the information, the IP address, and the type of apps accessing the device.
Defining policies and triggers is as easy as typing in a prompt. For example, "Detect user activity when PII data is modified" or "Detect user activity when Financial data is modified". These prompts enable triggers to monitor and alert when PII data or Financial Data is modified, respectively.
Insights into how information was accessed and by whom
After monitoring the activity and logging any violations, admins and monitors can easily browse the list of logged events. Associated with each event is information such as the user who accessed it, the database from which the information was accessed, and any other relevant metadata. This allows for quick checks to determine whether the event was a potential data breach or simply a false positive. In the case of a breach or mishap, a more robust security posture can be implemented.
Why choose DAM along with best DSPM practices?
Unlike DSPM, which primarily focuses on sensitive data stored in the cloud, DAM (Database Activity Monitoring) takes a comprehensive approach to safeguarding all types of data within an organization, not just data stored in cloud data stores. DAM ensures that data is protected from unauthorized access and manipulation, thereby reducing the risk of data breaches.
Rather than relying on maintaining security posture, DAM allows organizations to actively implement granular access controls, ensuring that only authorized individuals or systems can access and manipulate specific data. This helps prevent unauthorized access and reduces the risk of data misuse.
Robust monitoring and auditing capabilities enable organizations to track and analyze data access activities. This helps detect and respond to any suspicious or unauthorized data access, enhancing overall data security.
Moreover, DAM solutions assist organizations in meeting regulatory and compliance requirements by enforcing access controls, monitoring data access activities, and providing audit trails. This ensures that data is handled in accordance with industry standards and regulations.
Monitoring Database Activity with Adaptive
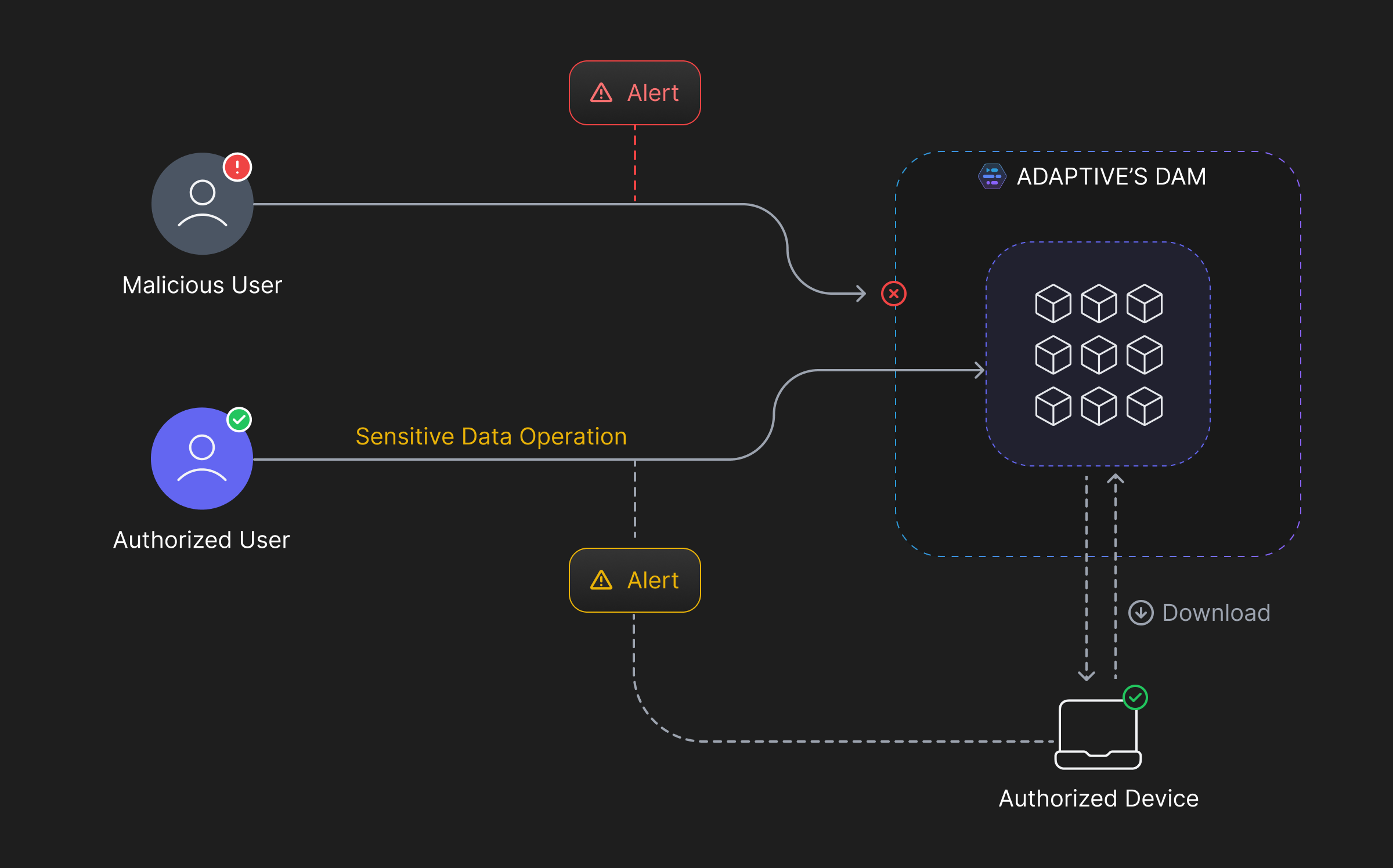
Adaptive offers database activity monitoring for all resources in your infrastructure. With Adaptive, you can -
Discover Sensitive Data - Define heuristics and automate the discovery of sensitive data across all your data stores. Once discovered, Adaptive can monitor and track every replica of the data, effectively preventing any unauthorized access.
Define Policies - After discovering labeled data, Adaptive effortlessly allows you to define policies and report violations. It alerts monitoring teams of any potential malicious activity, providing the necessary metadata to quickly identify the source of the triggered event.
Real-Time Monitoring - With Adaptive, you have the option to strengthen your organization's security posture by implementing real-time activity tracking and reporting. It helps monitoring teams discover vulnerabilities, potential breaches, or any other malicious activity as it occurs. Automated actions can be defined or strict actions can be taken against new threats.
 SOC2 Type II
SOC2 Type II