Identity and Access Management (IAM) explained

Introduction to Identity and Access Management
Identity and Access Management (IAM) is the branch of IT security that ensures that only authorized individuals in an organization have access to the resources they need to carry out their responsibilities. It forms a framework that helps govern and manage digital identities and data.
This can be categorized into three key components:
-
Creation and management of Users, roles, and policies
-
Authentication of users based on the unique credentials they identify with
-
Authorizing the user based on the role they are given
Intuitively, IAM can be achieved by defining the identities of employees, their roles, and the tools they require to perform their respective tasks. The same can be explained through the use of authentication and authorization mechanisms, such as passwords, Multi-factor authentication (MFA), Single Sign-on (SSO), and role-based access controls (RBAC).
IAM system simplifies the process of managing access to various applications, without requiring administrators to log in individually to each app. It also gives the organization a means to securely store identities and related data that can be used only when deemed relevant and necessary. The implementation of IAM can be done in many ways - on-premises, cloud-based, in a hybrid architecture, or through a third-party organization. The model that best suits any organization’s needs and architecture can be chosen.
Five Pillars of IAM
To provide increased security and a seamless IAM experience to the employees, there are five major factors that need to be considered. These factors are also referred to as the five pillars of Identity and Access Management.
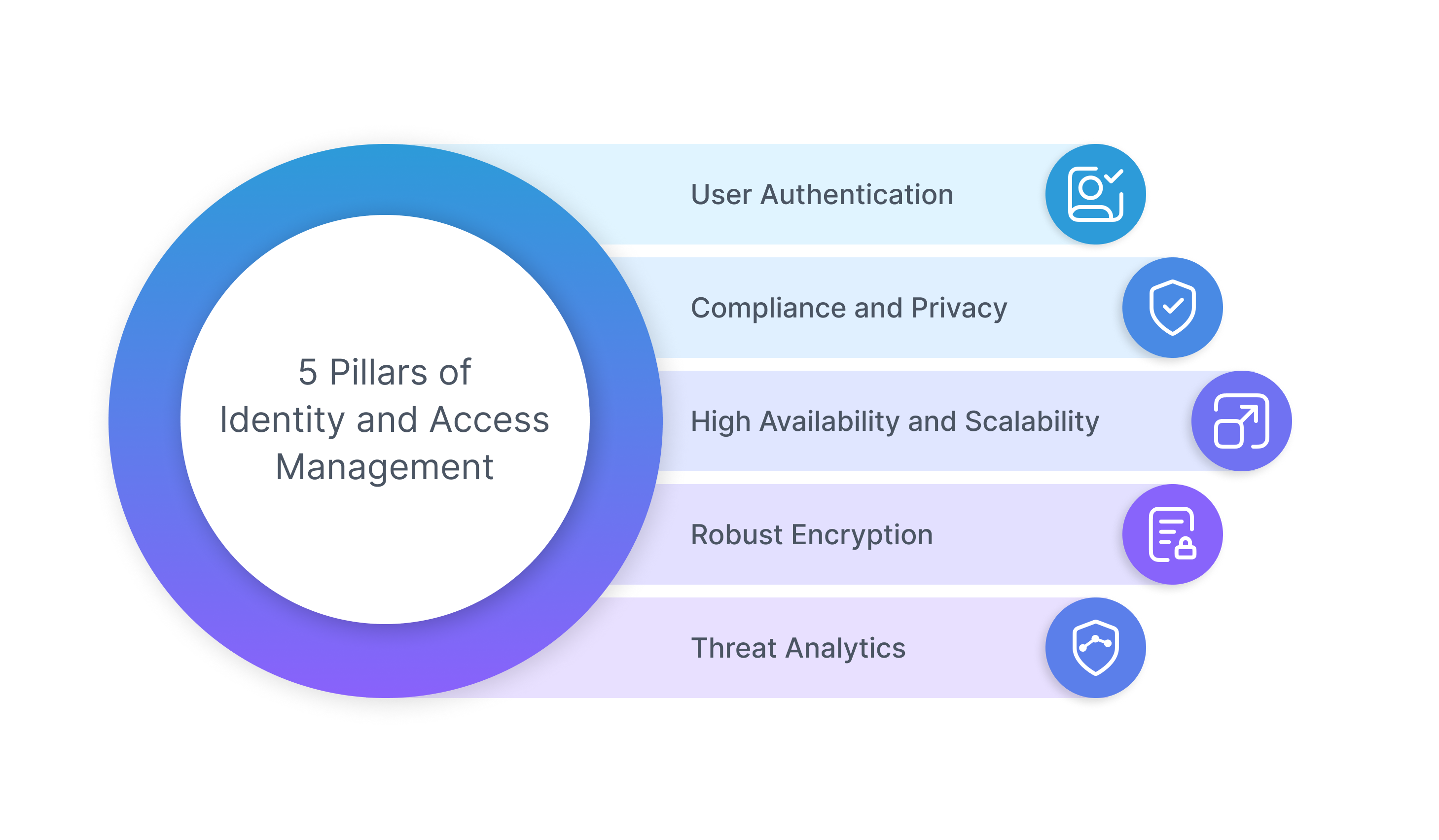
1. User Authentication
Securing the organization’s sensitive data and restricting access to its resources is one of the most important tasks. In today’s era of digital theft, it is essential for an organization to protect its business from external threats that can impersonate users to gain access to the organization’s resources. Therefore, the first important pillar of IAM is to have a reliable user authentication process to offer a smooth and secure login and access to its employees only.
All IAM solutions have a variety of user authentication mechanisms beyond just ID-password-based authentication. These can be One-time passwords (OTP), Time-based One-time passwords (TOTP), Biometric authentication, certificate-based authentication, etc. Employees can authenticate via the IAM system through these authentication mechanisms.
2. Compliance and Privacy
The organization must focus on compliance and establishing relevant privacy policies. All IAM solutions must follow standards like SOC 2, GDPR (General Data Protection Regulation - emphasizes an individual’s personal data and their right to data protection), HIPAA, COPPA, and other compliance updates to maintain the privacy rules and guidelines.
Transparency must be prioritized in an organization. What data is stored, and how it is stored must be detailed and made known to the users. After the GDPR, many countries have come up with privacy compliance and data retention policies of their own that the organizations must adhere to. Therefore, governing privacy policies and the latest compliance standards is another important pillar for IAM. While it seems to be too sophisticated and resource intensive, the organizations also benefit from an increase in customer trust and acceptance to share data.
3. High Availability and Scalability
For any IAM system, hundreds of individuals are expected to be identified and authenticated after verifying their digital identities and login credentials. While the mode of logging in might change between - remote and internal, the security posture remains the same. This authentication flexibility might not be part of certain IAM systems.
IAMs should have high availability, with their security postures and preventative measures to also handle irregularities in the stream. Also, with the growing organization size, scaling the IAM system to reach all users is a necessary pillar. This scaling up and down can be made manually through vertical and horizontal scaling. The investment must be made to research the loads expected by the IT infrastructure of the organization. Failover mechanisms and data backups must be in place.
Placing our focus on availability must not be an excuse to overlook the responsiveness and latency of the application(s) in question. Auto scaling can be employed, to save resources and money as well.
4. Robust Encryption
In any organization, data is both in rest and in transit during the course of its usage in the infrastructure. Encryption is a strong tool that enforces the protection of confidential information and the employee’s digital identities. Data servers can be included in the architecture to be either on-site or cloud-based.
Data in transit refers to the data being used to communicate with various infrastructure devices and servers. The data, irrespective of being in rest or transit, must be properly encrypted and stored in accordance with policies and compliance.
The comprehensive protection that this pillar offers can be confused as being part of the compliance and privacy pillar. Encryption is but a tool to adhere to certain policies, so compliance and policy adherence can be thought of as an abstraction of data security.
5. Threat Analytics
By processing user activities, the organization can make better-informed decisions, which help improve revenue growth and retain customers, making analytics the most important pillar of IAM. Organizations see vast potential in the capabilities of IAM in the field of business analytics and data visualization.
An IAM system must have the ability to record and generate reports on user logs, represent aggregate activities, and present them. The CISOs (Chief Information Security Officers) and other security experts of the organization may efficiently monitor the authentication and authorization data by utilizing these reports.
Most IAM systems also visualize these data trends to make key decisions for the organizations which can be categorized into 3 analyzing techniques: batch, real-time and predictive analytics. IAM's real-time and predictive analysis tools can be used to quickly identify various risks, employee profiles, privileges, fraud detection, risk-based authentications, and other important information. It also helps in upcoming events and attacks, allowing the business to mitigate or completely avoid any harm.
6 Key Benefits of IAM
Centralized Control
In a scenario where the user is compromised, central control via IAM allows an organization to compartmentalize access and contain the breach to all the impacted services.
Improved security
Enforcing least-privilege access with IAM allows users to have the minimum level of access necessary to perform their tasks. The granular level of access reduces the risk of security breaches and unauthorized access to sensitive information.
Compliance
Regulatory and governance requirements can be met by enforcing policies and centralizing access auditing via IAM to various services and resources.
Productivity
System admin tasks of managing users, access, and authorization matrices can be maintained in an automated way with IAM.
Scalability
As users and resources grow in an organization, IAM makes it easier to manage access, allowing you to scale your infrastructure as needed.
Flexibility
IAM enables us to create, modify, and delete access policies as needed, allowing you to respond to changing business requirements and security needs.
Challenges to IAM
Based on our research we categorize the challenges in Identity and Access Management as follows:
Complexity
The complexity of IAM depends upon the permutations and combinations of roles, resources, users, and privileges with which users should interact. For instance, AWS IAM is powerful but complex—its user guide is nearly 900 pages long. It is next to impossible to understand what existing policies do; in certain scenarios, organizations buy tools to just manage the policies of IAM.
Integration
Not all resources work seamlessly with all IAM systems. The granularity provided by resources often doesn’t match IAM roles and policies. These situations often require custom changes, thus extending implementation timelines from weeks to months to years.
User Adoption
If the users already had unrestricted access before the system, the IAM system can often create barriers within organizations. Also, many IAM systems do not have request-approval flows that can lead to access requests in the bureaucratic abyss.
Scalability
As the number of users and resources grows within an organization, managing IAM policies and access controls becomes increasingly complex, which can lead to leaky authorization and vulnerability if not managed.
Security
Ensuring the security of IAM systems and policies is crucial, as a breach in the IAM system could compromise the security of all resources.
Cost
Implementing and maintaining IAM systems can be expensive, and organizations need to balance the costs with the benefits.
 SOC2 Type II
SOC2 Type II