What is Network Access Control (NAC)?

Introduction
As of 2023, global internet traffic reached a staggering average of 4 million gigabytes per second. With ever-growing digital content, streaming services, and social media interactions, this number is only expected to increase. In the interconnected world, with data flowing in and out freely, network security has become all-important. Organizations handling sensitive data need to be careful to protect their network infrastructure from the prying public eye.
One such method for network security that has gained considerable prominence is Network Access Control (NAC). What makes a network secure and resilient? How do we achieve that? This article seeks to answer these questions by decrypting the intricacies of network security and access control.
What is Network Access Control (NAC)?
Network Access Control, (also known as Network Admission Control) is a comprehensive approach used by organizations to manage and regulate access to their network infrastructure (more often, their private networks). Simply, NAC ensures that only authorized users and registered/allowed devices are allowed to access the network resources, protecting the networks from threat vectors.
NAC revolves around 3 major principles: Authentication, Authorization, and Policy enforcement. Firstly, NAC systems authenticate users and devices to verify their identities and credentials and decide whether or not to grant access. Once authenticated, NAC transitions into a phase of authorization, where it enforces security policies on a very granular level. This ensures that the security and access standards pre-defined by the organization are met which can include software version verification, user roles, connection security, and adherence to protocols. Lastly, policy enforcement for these pre-defined standards in NAC involves continuous monitoring of network activities, ensuring ongoing compliance with the established security parameters. Any deviations from the defined policies trigger immediate responses, such as access restrictions or alerts to network administrators thus preventing unauthorized access.
NAC Architecture
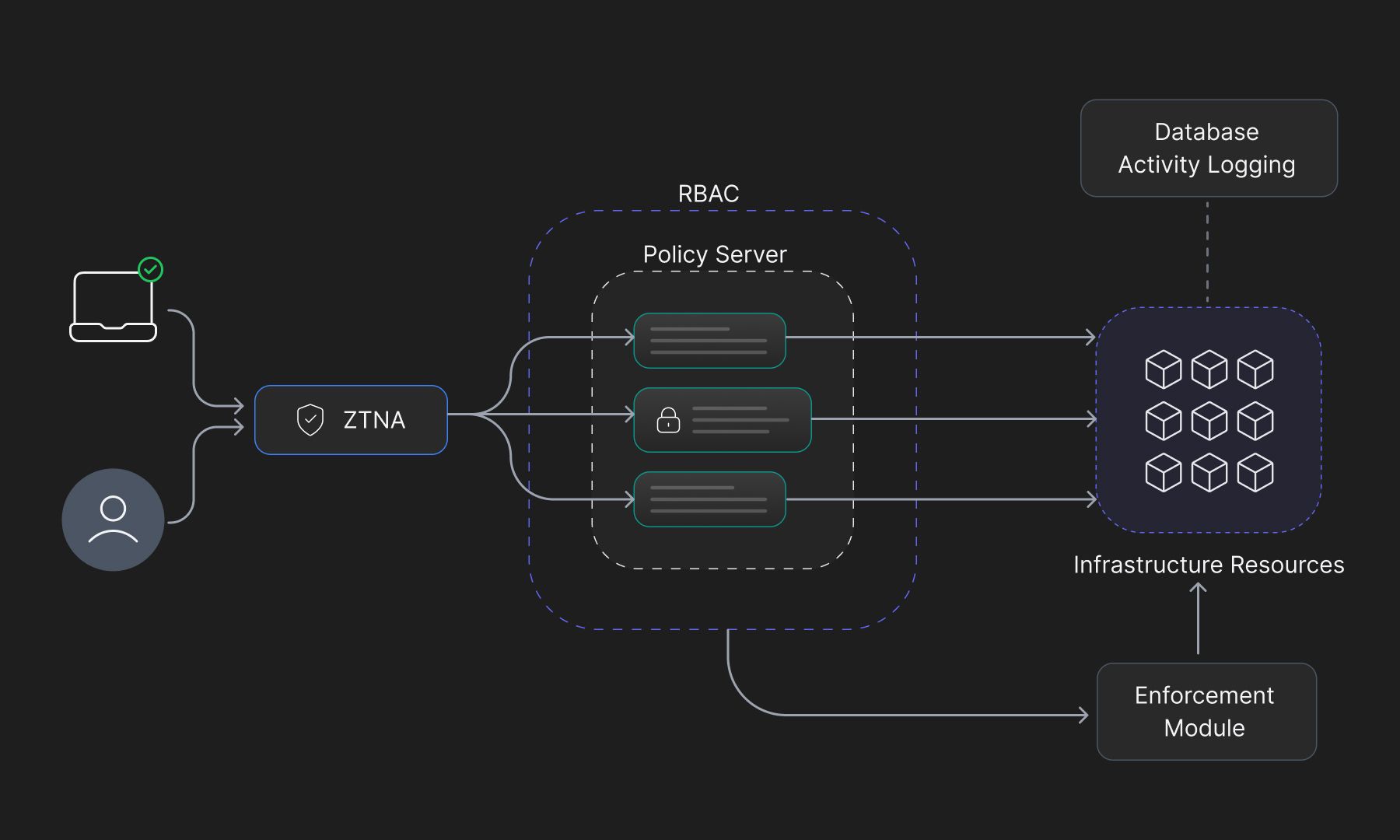 Network Access Control has several key components that work in tandem. The architecture of NAC changes from organization to organization and depends on many factors, such as cost, scalability, integration capabilities with current network infrastructure, required response mechanisms, etc. But NAC as a whole can be divided into a set of non-overlapping services which are listed below:
Network Access Control has several key components that work in tandem. The architecture of NAC changes from organization to organization and depends on many factors, such as cost, scalability, integration capabilities with current network infrastructure, required response mechanisms, etc. But NAC as a whole can be divided into a set of non-overlapping services which are listed below:
-
Authentication Mechanisms: This component handles user authentication and device validation. Usernames, passwords, MFA, etc. can be the various ways for authentication.
-
Policy Server: This is the crux of the NAC system, where security administrators define and manage the aforementioned policies helping in Role-Based Access Control.
-
Endpoint Assessment: This component performs compliance checks on devices to verify their adherence to organizational policies and to the endpoint access.
-
Enforcement module: This helps enforce the policies pre-defined and set in the policy server by the security administrators.
-
Logging and Reporting module: It provides comprehensive insights into the logging and network activities that aid in threat detection and compliance audits.
-
Network Segmentation: This is an optional service that is used to divide the network into segments (or Virtual Networks) based on the organization’s requirements. This helps limit the lateral movement of threat vectors in case of data breaches in one of the V-LANS.
Network Access Control emphasizes on the principle of least privilege, ensuring that users and devices have the minimum necessary access to network resources. NAC achieves this by authenticating and authorizing users and devices before granting access, aligning with Zero Trust's core principle of "Never Trust, Always Verify". Additionally, aligning with the nature of Zero Trust architecture, NAC continuously monitors network activities, allowing organizations to dynamically adjust access privileges based on real-time risk assessments.
Throughout this article, we use the term device interchangeably with users. While it is the user who makes the conscious decision to access a network, it is through (one of their many) devices that they do so. Even if the user is authorized to use a network, the device may be a potential risk if it is non-compliant. So, in the context of networks, it is apt to use devices instead of users and this is the norm followed from this point.
Types of Network Access Control
Network Access Control solutions can be categorized into two primary types depending on the distinct purpose they are used for in the security landscape.
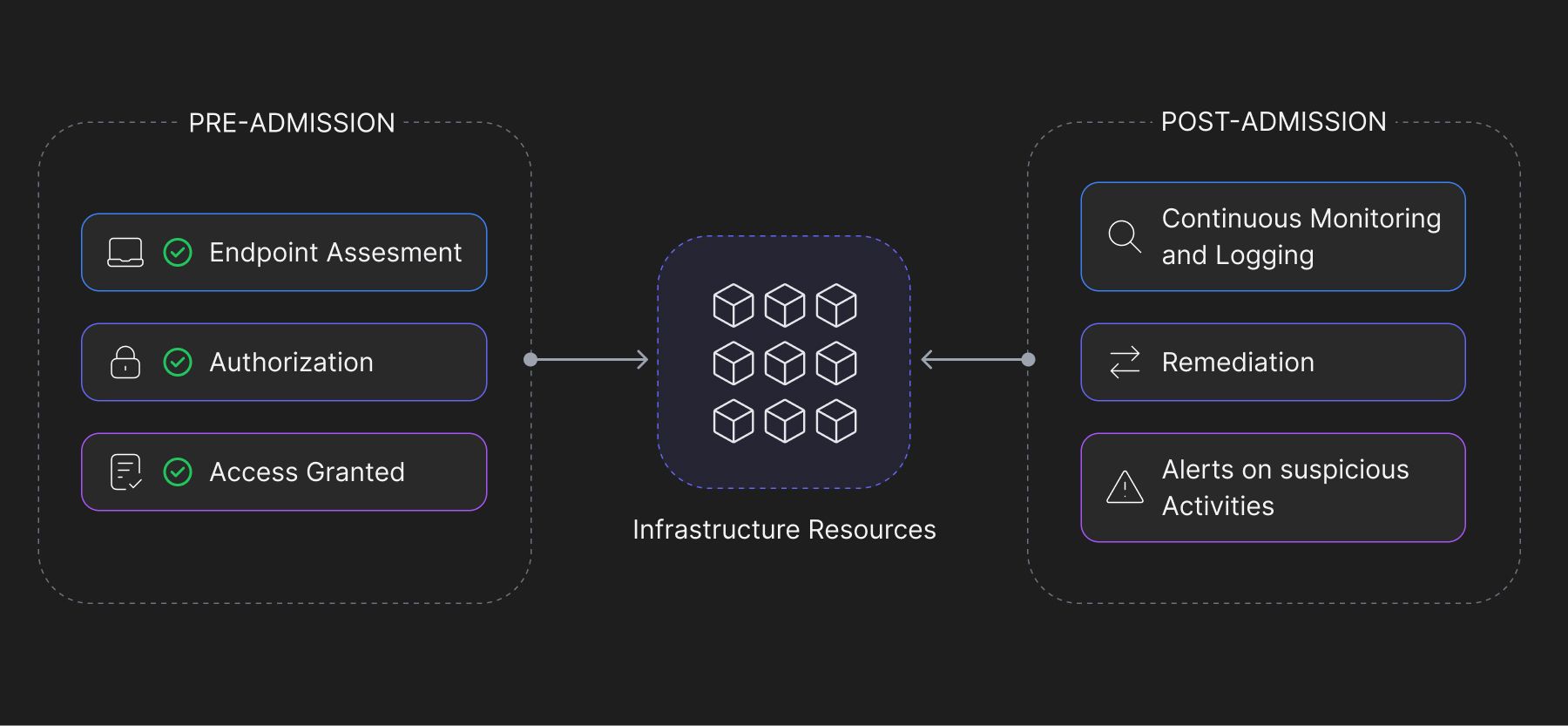
1. Pre-admission NAC
Pre-admission NAC, also called Pre-connect NAC, focuses on the authentication and authorization of users and devices before they are given access to the network. It checks the identity, security posture, and compliance with the organizational policies of the user.
The key steps involved in pre-admission NAC are:
- Endpoint Assessment: Conducts a comprehensive compliance assessment of the connecting device to check if it meets the defined security and policy requirements.
- Authentication: Authenticating the users or devices seeking access to the network to ensure only authorized users are allowed to connect.
- Policy Enforcement: Based on the policies defined by the policy server, the user’s access to the network is allowed or denied.
Use case: Pre-admission NACs are often used as an initial line of defense, it safeguards the private networks of an organization, especially in case of third-party vendor or guest access.
2. Post-admission NAC
Post-admission NAC also known as post-connect NAC focuses on continuous monitoring and regulating devices and users already connected to the network. Unlike pre-admission NAC, post-admission NAC ensures that the access to users applies to other parts of the network as well and they cannot jump laterally within the networks to other segments without proper authorization.
The key steps involved in post-admission NAC are:
- Continuous Monitoring: Post-admission NAC continuously monitors the user's and device’s activity in the network, detecting any changes or anomalies.
- Remediation: If a non-compliant device is found, a post-admission NAC solution can initiate remediation sequences, which may include quarantining the device, updating security patches, or applying global restrictions until the issue is resolved.
- Real-time Threat Response: As soon as a threat is detected, the NAC solution alerts the administrators (after the remediation activities), and implements appropriate measures to isolate and monitor the threat.
Use case: Post-admission NAC maintains a proactive approach to security, by monitoring, detecting, and responding to threats after the devices have gained access to the private networks.
Importance of Network Access Control
With evolving attack vectors and threat landscape, it’s becoming more important for organizations to streamline their security practices and better monitor and control access to their network. A few ways in which Network Access Controls are important for this are -
1. Evolving threat vectors/landscapes
Cybercriminals are using new ways to exploit vulnerabilities in networks and gain unauthorized access to sensitive and confidential information. Malware, ransomware, phishing attacks, and insider threats are just a few examples of the growing threats that organizations must combat.
NAC provides a comprehensive defense mechanism by enforcing security policies, verifying device compliance, and authenticating users before granting network access helping combat the growing threat vectors.
2. Limitations of Traditional Security Methods
Traditional security methods like firewalls and antivirus software, while crucial for network defense and endpoint protection, have inherent limitations. These solutions struggle to detect and prevent insider threats, and handle the diverse device landscape threats created by BYOD (Bring your own device), and the growing IoT sector.
They also lack granular control for preventing lateral movement within the network. Whereas in the case of NAC, there are components that help counter these limitations.
3. Risk Mitigation Associated with Unsecured Devices
Network Access Control (NAC) plays a crucial role in mitigating risks linked to unsecured devices. In an era of rampant cyber threats, ensuring that only authorized and secure devices gain network access prevents potential breaches and data compromises. By identifying and restricting unsecured devices, NAC acts as a robust defense, fortifying the network against external attacks.
4. Meeting Regulatory Requirements Regarding Network and Data Security
Compliance with regulatory standards is non-negotiable for organizations. NAC ensures that networks adhere to stringent security protocols mandated by regulatory authorities. By enforcing these standards consistently, businesses avoid legal complications and demonstrate a commitment to safeguarding sensitive data. NAC acts as a compliance assurance tool, ensuring organizations meet the necessary regulatory requirements.
5. Managing Guest and Visitor Access to a Network
With increasing mobility and collaborative work environments, managing guest and visitor access is paramount. NAC provides a secure framework for granting limited and monitored access to guests. It ensures that visitors can connect to the network without compromising its integrity. By segregating guest traffic and setting specific access parameters, NAC maintains the network's security while accommodating external users.
6. Effective Device Management and Network Access Privileges
NAC simplifies device management by offering granular control over network access privileges. It allows organizations to define specific access levels based on user roles, device types, and security clearance. This fine-tuned control not only enhances overall security but also optimizes network resources. By managing device access effectively, organizations streamline operations while minimizing security risks.
7. Providing Information in case of Incidence Response
During incident responses and forensic investigations, timely and accurate information is paramount. NAC serves as a valuable asset in these scenarios by providing detailed insights into network activities. It records user actions, device interactions, and access patterns, aiding security professionals in analyzing incidents and conducting thorough forensic investigations. This information is invaluable in understanding the scope of a security breach, enabling organizations to bolster their defenses and prevent future incidents.
The limitations highlighted can be remediated by using a firewall as well. So why Network Access Control? NAC and firewalls are both crucial components of network security, but they serve different purposes and offer distinct functionalities. Understanding the differences between NAC and firewalls is essential for establishing a comprehensive security strategy. Let's explore the disparities between these two security measures.
Network Access Control vs Firewall - What is the difference?
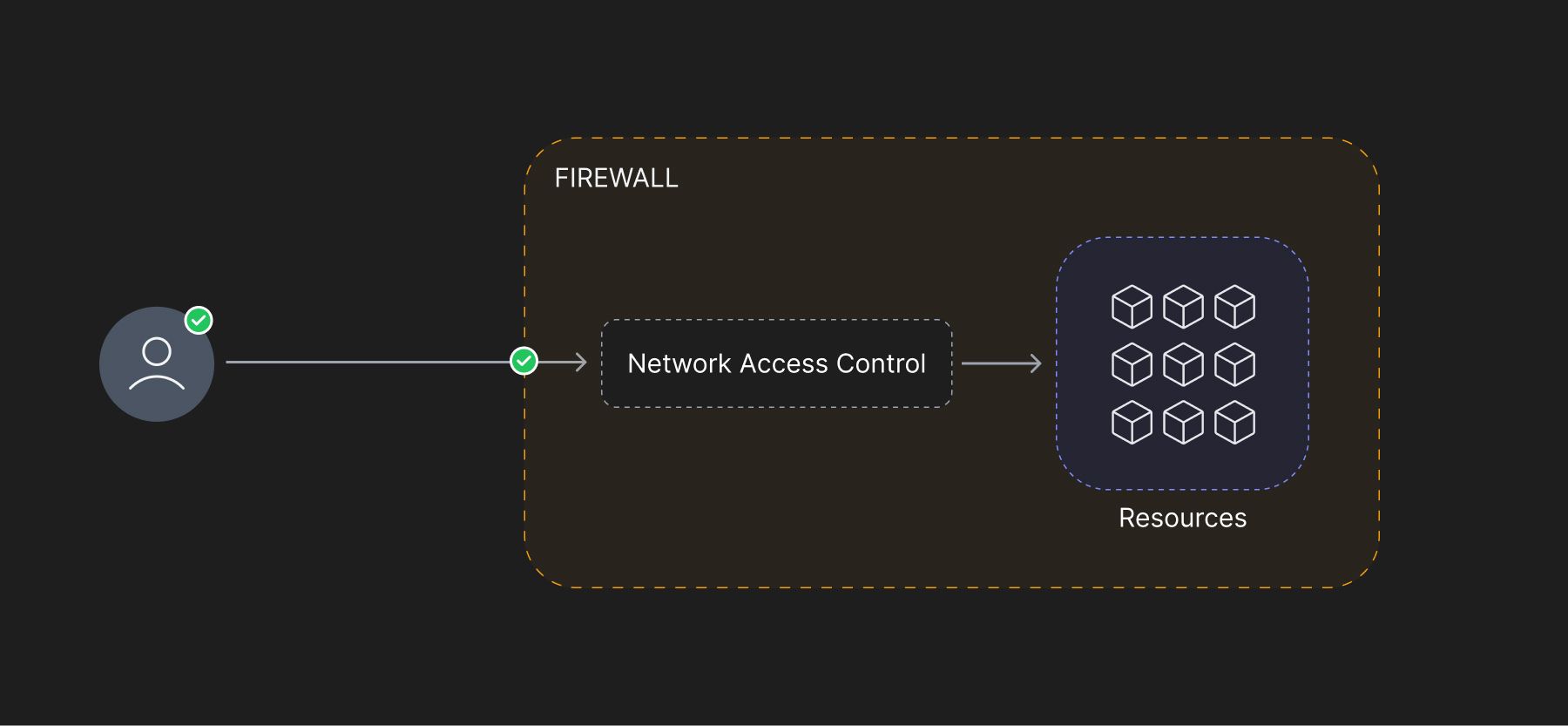 Network access control and firewalls both are important components in network security but are very different in terms of their functions and the way they operate. Let's divide the scope of exploration into 3 distinct categories and then understand how the two solutions differ.
Network access control and firewalls both are important components in network security but are very different in terms of their functions and the way they operate. Let's divide the scope of exploration into 3 distinct categories and then understand how the two solutions differ.
1. Functionality in network infrastructure
- NAC: Focuses mainly on controlling and managing the endpoint access in the network by verifying user identity, device compliance, and enforcing security policies. It ensures that only authorized users and devices gain entry, reducing the risk of unauthorized access and potential threats.
- Firewalls: Primarily serve as a barrier between networks, controlling incoming and outgoing network traffic and inter-network communications based on predefined rules. They monitor and filter network traffic to allow or block specific connections based on pre-defined rules.
2. Scope of Protection
- NAC: It operates at the endpoint level, focusing on users and device-level access control. NAC ensures that users who are allowed entry to the network meet certain security requirements and get access based on their compliance status, identity, and device type.
- Firewalls: It operates at the packet level, and provides network-wide security by monitoring and filtering traffic in the network perimeter. A firewall regulates access to devices within the network with continuous monitoring based on predefined policies.
3. Granularity of control
- NAC: It offers granular control over user and device access, allowing organizations to define and enforce specific security policies based on user roles, device types, or other parameters.
- Firewalls: It provides a broader level of control, focusing on network traffic filtering based on IP addresses, ports, and protocols. Firewalls do not differentiate based on user and device identity and hence have lesser granular control.
While NAC and firewalls have distinct functionalities, they are often used together to establish a robust and advanced security framework. Network Access Contol complements Firewalls by providing enhanced access control and user/device authentication, while firewalls, on the other hand, protect the network perimeter from external threats and filter traffic based on predefined rules.
Use cases of Network Access Control
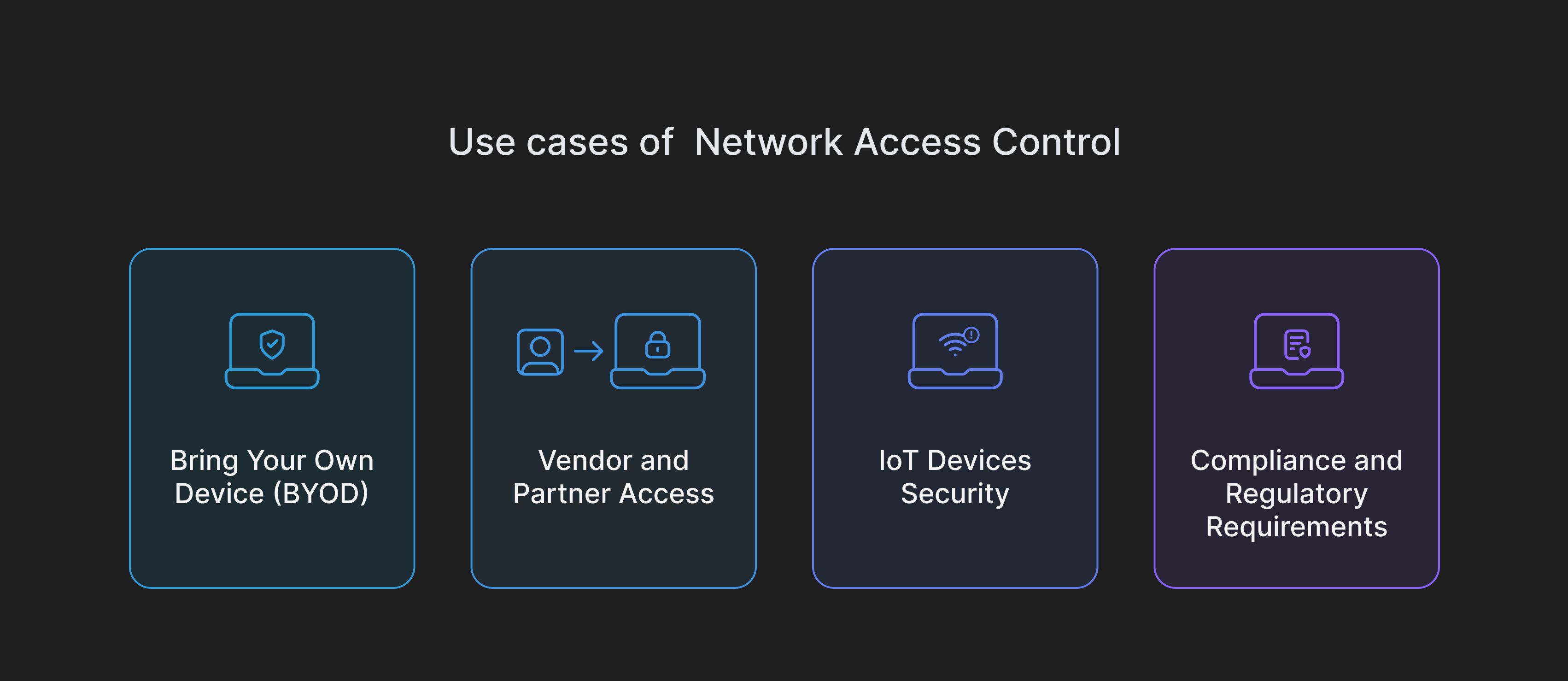
Network Access Control has a lot of applications in various use cases. Some of the most important use cases of NAC are:
1. Bring Your Own Device (BYOD)
With more remote work being adopted across organizations, employees using their personal devices to access an organization’s network infrastructure has become a common practice. However, having an NAC for BYOD ensures that accessing the private network from the comfort of remote work doesn’t require any sacrifice on security. NAC helps meet security standards, enforce compliance checks, grant access based on the device’s security posture, and restricts compromised devices from accessing the network.
2. Vendor and Partner Access
Managing access for non-employees such as vendors and partners gets easy with NAC in place. NAC only allows access to non-employee devices that meet defined security standards, provide limited-time access to necessary resources, and ensure network segmentation to protect internal resources and sensitive information.
3. IoT Devices Security
Internet of Things (IoT) devices are gaining widespread usage and these devices provide more access points to external threats. NAC helps extensively profile these devices easily without any manual provisioning. NAC makes IoT devices to be segregated from accessing critical resources, complies with security policies, and also mitigates risks involved with compromised devices.
4. Compliance and Regulatory Requirements
NAC helps organizations in highly regulated industries such as Financial Services, Healthcare, and Insurance to stay compliant with standards such as HIPAA, SOC 2, GDPR, SOX, and even PCI. These organizations deal with sensitive PII and PHI information that require implementing restricted access to such information. NAC allows limiting only privileged users to access sensitive information, setting security policies, auditing network access, and easier generation of audit reports.
Advantages of Implementing Network Access Control
1. Improved Network Visibility and Control
NAC provides organizations with enhanced visibility into network activity by continuously monitoring user and device behavior. It detects anomalies, if any, and also acts in real time to alert administrators. With granular control over network access, NAC allows organizations to enforce security policies and ensure that only authorized users and compliant devices can access critical resources.
2. Enhanced Access Control and Authentication
Depending on the implementation, NAC can use various authentication methods, such as username/password, digital certificates, or multi-factor authentication, ensuring that only authorized individuals can connect to the network.
3. Device Compliance
The policies that are instrumental to the organization can be enforced on every device that can access its network. This increases security and reduces the area of threat vectors to act from.
4. Security Posture Assessment
Based on the policies enforced and the authentication mechanisms in place, the organization can have a good idea about the security posture it is currently using. By monitoring the threats, the organization can make informed decisions about the security posture and make appropriate changes to strengthen its security.
5. Enhanced Incident Response and Threat Mitigation
With its continuous monitoring and real-time threat detection, NAC enables organizations to respond swiftly to network incidents. By quickly identifying and isolating compromised devices, NAC minimizes the spread of threats and facilitates efficient incident response.
6. Mitigation of Insider Threats
Insider threats, whether intentional or accidental, pose significant risks to organizations. NAC addresses this by continuously monitoring user behavior and detecting anomalies that may indicate suspicious activities.
7. Network Segmentation and Lateral Movement Prevention
This advantage depends on the components employed in the NAC system as described in an earlier section, but NAC can be used in implementing network segmentation, dividing the network into smaller, isolated segments. This limits the lateral movement of threats within the network, preventing attackers from freely traversing the organizational landscape if they gain unauthorized access, and enter the network.
8. Compliance
Compliance with standards and policies is crucial in evaluating the long-term sustainability of an organization. NAC can help in meeting compliance requirements by enforcing security policies, maintaining audit trails, and providing granular control over network access.
Final Thoughts
Network Access Control is a good part of the solution to improve an organization’s complete security posture. For infrastructure setups with segmented networks and the right access policies in place, NAC provides auditable visibility of the devices accessing the network.
However, NAC security has some limitations when it comes to providing specific granular access control over individual endpoints. Having a good data security posture along with access control is equally important for organizations to safeguard against bigger threats. Adaptive’s data security platform comes with secure features such as data monitoring, classification, and data loss prevention to help improve the overall security posture. The platform's Just-in-time access management feature helps implement role-based access controls for all users and guests faster.
 SOC2 Type II
SOC2 Type II