Why the world needs to rethink Infrastructure Access?

The Increasing Data Breach Problem
The problem of cyber breaches is only getting worse by the day. The best way to understand a trend is to view it through the lens of numbers. Numbers don’t lie.
- The average cost of a breach has increased to $4.35M
- In the US alone, the number of data breaches has gone up from 785 breaches in 2015 to over 1802 breaches in 2022.
- 54% of organizations have experienced a cyberattack in the last 12 months
In addition to the above statistics, the global geopolitical situation is tense. Gone are the days when organizations had the luxury of considering cybersecurity as a secondary spend on the balance sheet. In the current times, companies cannot wait to establish a good security posture until the need becomes tangibly clear. If the need turns urgent, it's likely already too late.
The increase in data breaches has made it clear that traditional security measures are no longer enough. We need a more adaptive and secure solution that can protect against modern threats.
Insider Threat: a new problem within organizations
Recently, a new type of threat has started impacting organizations - Insider Threats. An Insider Threat refers to a cyber security risk that originates from within the organization. This doesn’t only include a bad actor, but also accidental operations or phishing victims. Insider Threat actors could be managers or executives, regular employees, or contractors. In order to understand the severity of Insider Threat, let’s first look at it by the numbers:
- 60% of data breaches are caused by insider threats (Goldstein, 2020).
- Over the last 2 years, Insider incidents have increased by over 47%
- The average annual cost of insider threats has skyrocketed in only two years, rising 31% to $11.45 million (ObserveIT, 2020).
The majority of insider threats within organizations stem from unsupervised access to IT infrastructure. About 63% of organizations think that privileged IT users pose the biggest insider security risk to organizations. This is due to the fact that modern IT infrastructure has become ephemeral, fragmented, and much more complex.
Complexity of the Modern-day Infrastructure
In order to understand the problems with infrastructure access, it is important to first know what makes it so complex. There are a few recent trends in the tech industry, that have changed the operating paradigm of the world, not just for people, but for organizations.
Remote-first trend post-covid
In March 2020 Covid struck, and remote work went mainstream in an unnaturally rushed timeline, and the consequence was organizations not getting enough time to think through all the processes needed to adapt to this change sustainably; forcing them to rethink infrastructure access
Increased Cloud Adoption
A common infrastructure setup that companies used in the pre-cloud era was setting up an on-premise server and a perimeter network to restrict access. However, the onset of cloud adoption has changed how infrastructure is set up resulting in the need for new access policies.
Due to the cloud and remote-first movements, infrastructure can no longer be looked at as a static entity, but rather as a dynamic and ephemeral system. This forces organizations and infrastructure teams to reimagine access.
Compliance audits enforce better security posture and auditability in infrastructure access
Compliance audits including SOC-2, ISO 27001, HIPAA, and SOX have become table stakes for companies of all sizes. Historically, early-stage companies were typically exempt from these compliances but that’s not the case anymore. As a part of compliance, organizations need to be able to audit all infrastructure access and attribute every query/ command to an identity within the organization. This need for auditability has compelled organizations to rethink their infrastructure access strategy.
Security by Obscurity
One of the postures organizations take is ‘NO ONE in the organization has any infrastructure access and hence we are SUPER secure’. This posture practically never works in the real world. What happens when something goes down? How is downtime resolved? What if someone needs to access specific data? The reality is that someone in the organization has to have access to infrastructure, and by nature of that, the access strategy needs to be intentionally and carefully thought through.
The Core Infrastructure Access Problems
Now that we understand the trends that make modern infrastructure complex, we can dive into the actual access-related problems that have resulted in increased breaches.
The Problem of Privilege Abuse
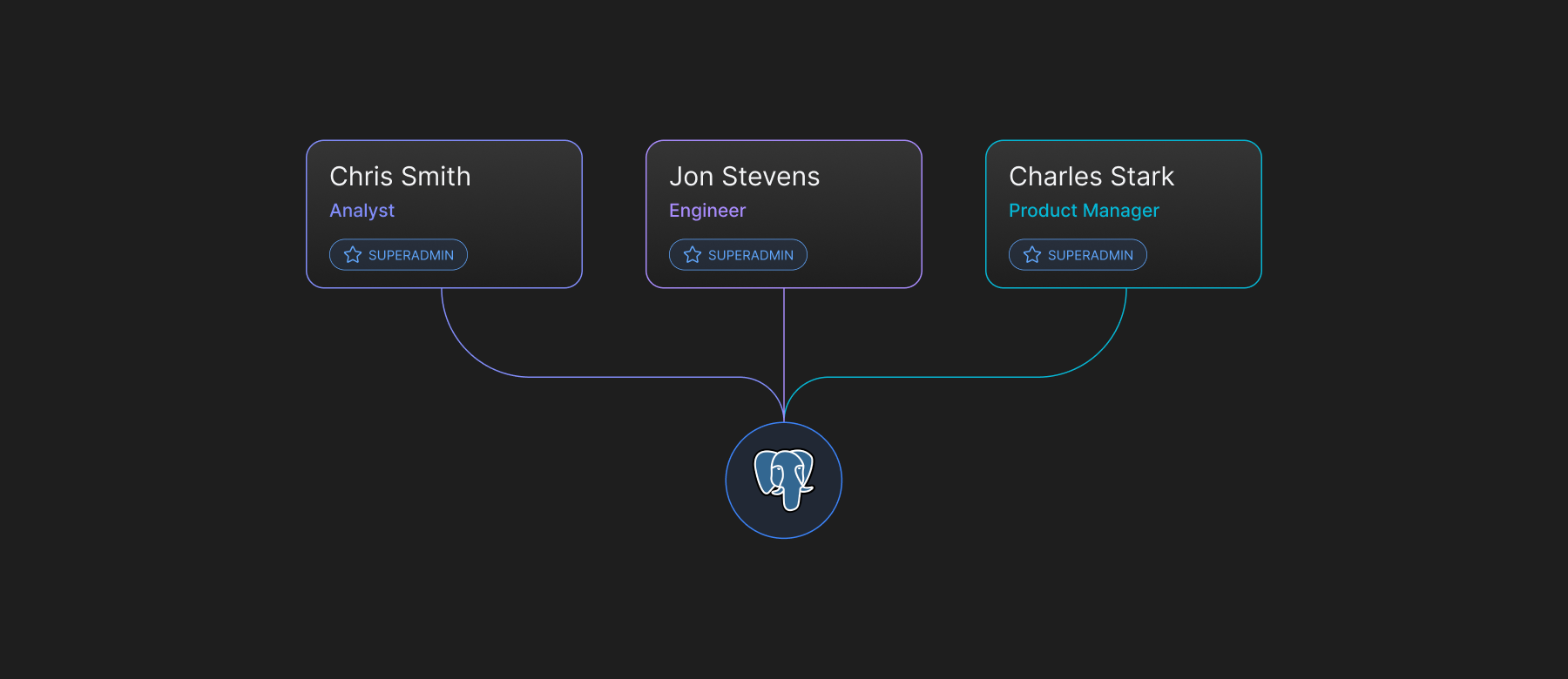
How many times have you heard organizations say, 'Everyone has access to everything, but we’ll clean this up when the time is right'? This is one of the biggest access-related negligences we see in organizations. About 21% of breaches happen due to elevated privileges.
So if clearly elevated privileges are a problem, why don’t more companies implement the Principle of Least Privilege? The answer is that it’s an extremely challenging and cumbersome framework to practice at scale. The cloud IAMs are unable to configure privileges in the downstream infrastructure resources like databases, VMs, K8s clusters, etc. Thus to assign any privileges, DevOps and SRE teams have to configure them at the resource level, which becomes extremely complex to manage at scale. This is the reason why the Principle of Least Privilege becomes hard to implement within organizations, and they go back to managing users at the IAM level in an all-or-nothing privilege framework.
The Problem of Credential Sprawl
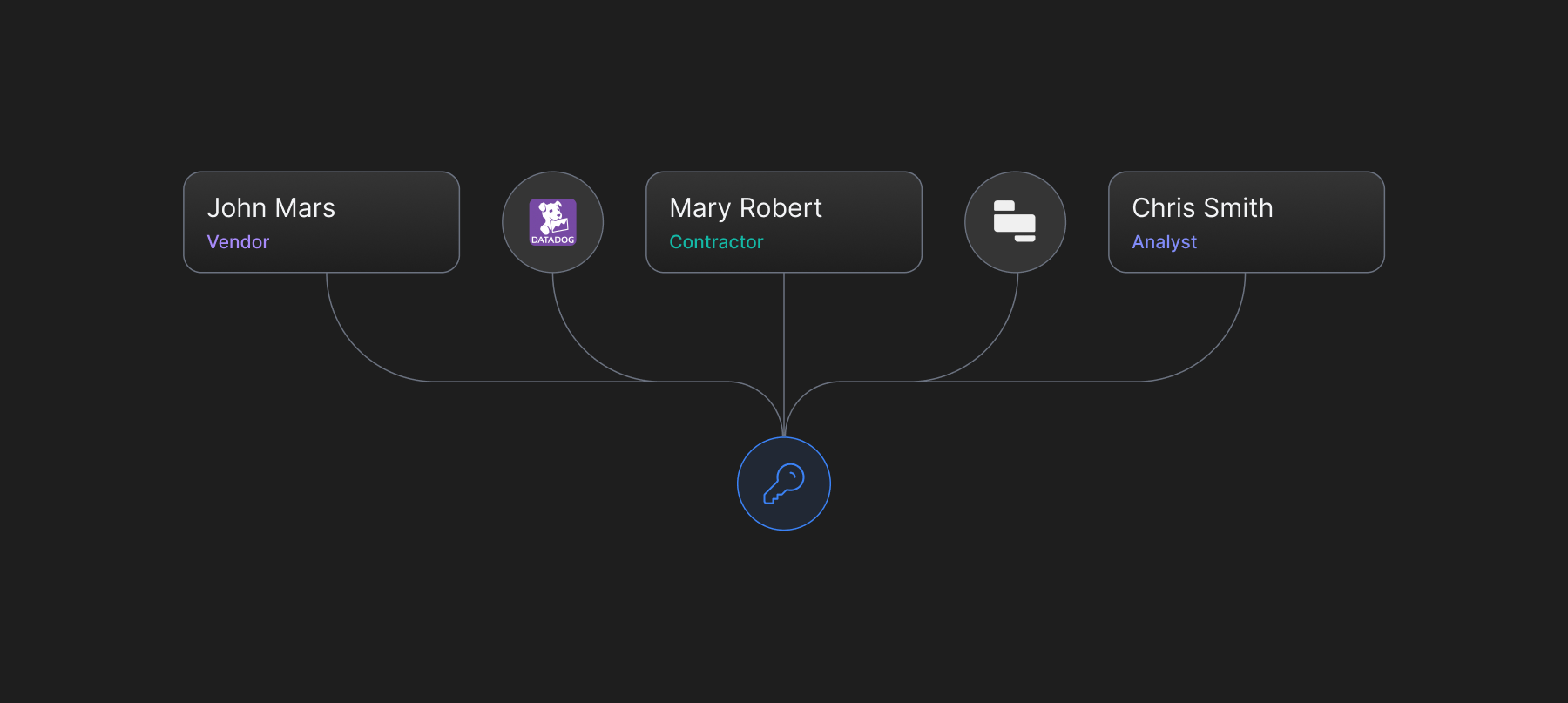
Sharing infrastructure credentials is one of the most high-risk practices within any organization. While not many organizations will admit to this, infrastructure resource credentials are often shared as plain text on Slack or other internal communication tools, which opens up one of the riskiest threat surface areas. Once a credential is shared, it's hard to trace and manage where it ends up and is particularly susceptible to accidental leakage, phishing, and insider threat.
So you may ask why not implement SSO? Infrastructure resources such as databases do not natively support SSO. Thus configuring SSO on infrastructure resources is an extremely difficult task, especially at scale when you have a larger infrastructure.
The Problem of Network Sprawl
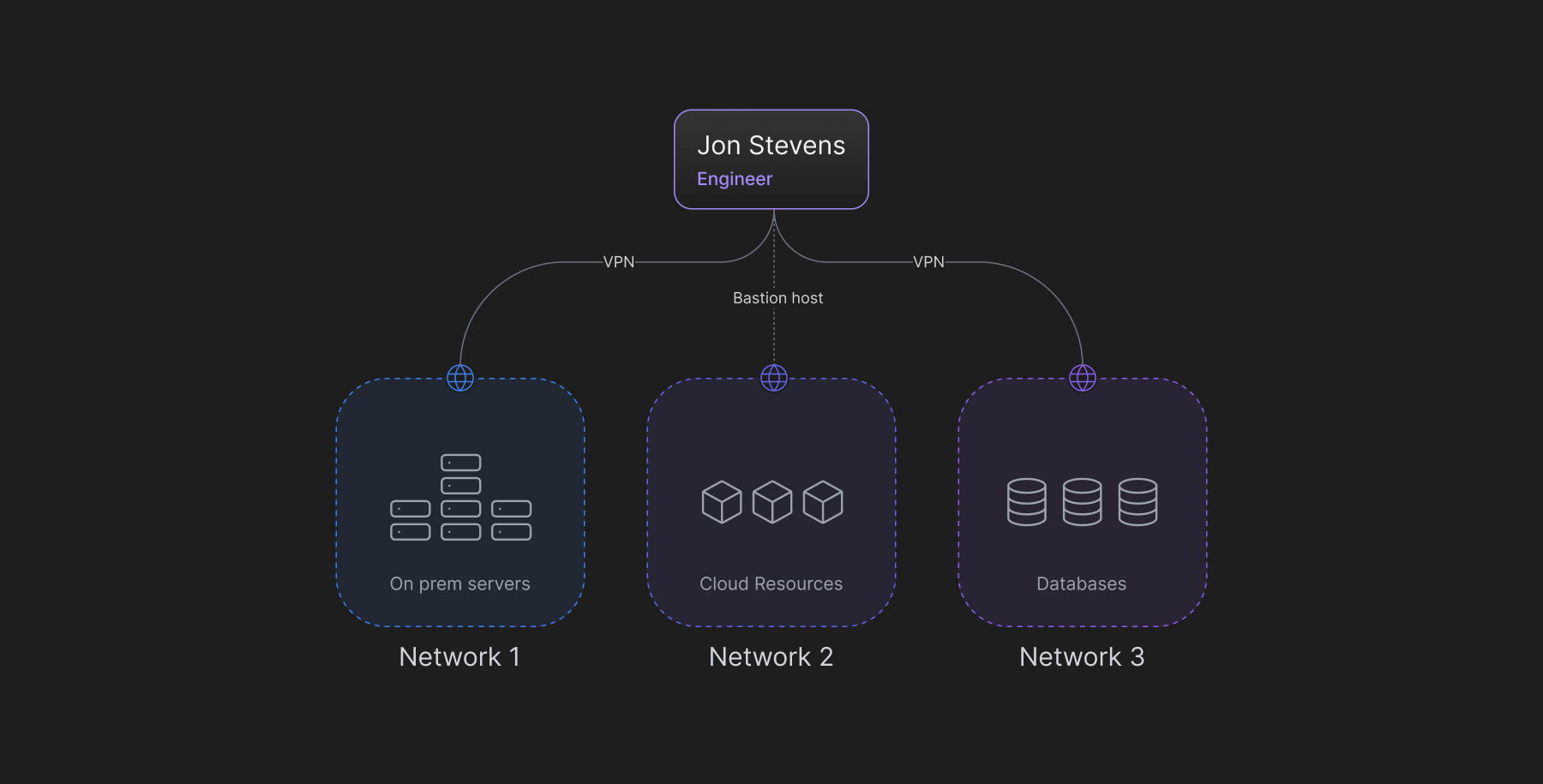
Network sprawl is a phenomenon resulting from the growing adoption of the cloud, and subsequently, hybrid IT, where some applications and infrastructure remain on-premise, but some are transitioned to the cloud. Due to hybrid IT, the number of networks an organization relies on -- those that are on-premises combined with those owned by cloud and SaaS providers -- is growing rapidly, and potentially unchecked, as more and more infrastructure moves to the cloud and business units implement more SaaS applications.
Traditional networking tools such as traceroute are becoming obsolete, as they are typically blocked from accessing service-provider networks. At the same time, cloud monitoring tools don’t have visibility into on-premises infrastructure performance -- nor should they, as some would argue. So, the environment is becoming more opaque - making access more complex.
Given the above problems, securing infrastructure resources, especially from an access perspective has become a huge challenge for organizations.
Limitations of Existing Solutions
Given the above tailwinds, the modern-day infrastructure access management platform needs to be built to meet the following criteria:
- Implement the Principle of Least Privilege
- Abstract Resource Credentials
- Secure and Scalable Network Management
Generally, security practices lag technology advancements by a few years. And this is the reason a lot of the existing solutions we rely on cannot meet the above criteria.
Conventionally, accessing resources necessitated two key pieces of information: the location of the resource (network) and the necessary credentials for the connection. However, most existing software tools in the market address only one of these requirements, inadvertently, making the neglected dimension into a potential security vulnerability.
VPNs have become obsolete
VPN is ubiquitous and almost every organization uses one. Historically, VPN was great when organizations only cared about protecting servers located on-premise. Modern-day infrastructure, on the other hand, is on-cloud, ephemeral, and collaborative - and that is where relying on VPN becomes complex and cumbersome. Unlike modern cloud services, VPNs were not designed to scale to meet higher demand. As distributed workforces grow, this can increase latency and performance issues for remote users.
Additionally, most VPN setups grant total access to users, rather than granting access based on an individual user’s identity and role. This can open the door to unsanctioned lateral movement within the network and put sensitive data at risk. This also means that providing infrastructure access to a third-party vendor or a contractor can be painful and slows down the process of granting access. Lastly, without centralized, application-specific logs, IT teams cannot view which applications users have accessed or track the actions they have taken within those applications — making it that much harder to protect sensitive corporate resources or trace an attack. Organizations that aim to scale while enhancing security and achieving granular traceability over resources seek to eliminate the need for a VPN solution.
Bastion Hosts are difficult to manage
A Bastion Server is a specialized computer used to access an infrastructure resource and helps create a separation between the downstream resource and developers. From a security perspective, a Bastion host is the only node in the network exposed to the public. While Bastion hosts are extremely popular, they have their fair share of limitations and challenges. Bastion hosts bring a huge amount of maintenance overhead as these nodes provide a single entry point to accessing the downstream infrastructure resources, and hence also end up becoming a single point of failure. If your bastion host goes down, guess what, none of the downstream resources can be accessed.
Existing Access Management tools are too expensive and too difficult to set-up
The majority of the existing infrastructure access management tools were built for the server era where infrastructure was on-premise. However cloud adoption has accelerated even in regulated industries such as Finance and Healthcare, and that has made it challenging to implement the legacy infrastructure access tools as they don’t work easily with cloud environments.
Moreover, a lot of the tools are built on an agent-based architecture and primarily serve large enterprises. Installing an agent in every target resource not only makes set-up and maintenance extremely time-consuming and complex but also has a foreign agent run in your target resource which presents a vulnerability; thus ironically beating the purpose of solving a security problem.
About Adaptive
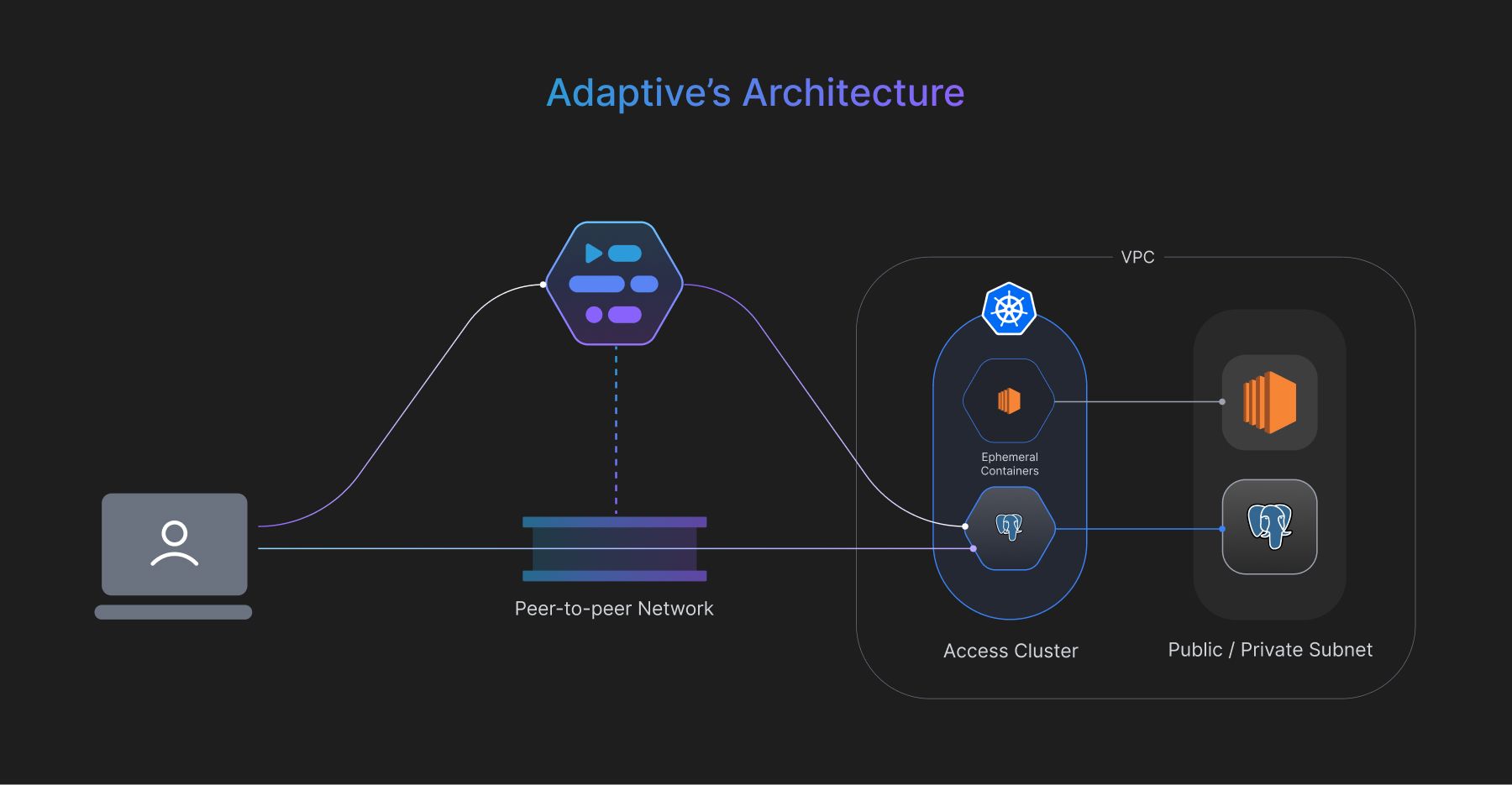
In order to solve the above gaps in the market, we built Adaptive - a Just-in-Time access management platform with native network access control. To address the shortcomings of traditional security software, we designed our solution from a modern, dev-first perspective and one that can adapt to the dynamic nature of cloud infrastructure.
Adaptive’s container-based architecture allows organizations to deploy a zero-trust solution at scale without needing to make architectural, hardware, or software changes. The platform creates ephemeral secure tunnels to connect with infrastructure resources in any network across different VPCs, improving the organization’s security posture and increasing granular auditability for compliance.
Adaptive does not reveal the real resource credentials and securely allows access through ephemeral credentials to infrastructure resources from a centralized platform via Adaptive CLI, browser, or any other client tools.
Conclusion
Privileged Access Management platforms, historically tailored for the enterprise sector, have not adequately addressed the unique needs of the early-stage and mid-market sectors. As cloud adoption surges and compliance becomes non-negotiable, there's a growing demand for innovative infrastructure access solutions in these markets. Current offerings, based largely on agent-based architectures or demanding specialized networking expertise, fall short of serving the mid-market effectively. It's crucial to adopt a developer-first approach to infrastructure access—one that's straightforward to implement, scales seamlessly with infrastructure and operates externally to target resources. To address modern challenges, we must introduce a new paradigm for infrastructure access.
 SOC2 Type II
SOC2 Type II