4 Unique Ways to Monitor Database Activity without Fault

The adoption of Cloud systems and the rise of remote workforces have made traditional database activity monitoring techniques using network-based agents ineffective. While these techniques worked well for on-premises environments, they fail to monitor activities on cloud database instances due to the increased access points. Furthermore, solutions based on native database application logs are not feasible due to the high storage and bandwidth costs, especially for organizations with extensive infrastructures.
To offer comprehensive coverage across various cloud and on-premises environments and to effectively capture all potential use-cases and build fail-safes, DAM can be implemented with one of the following 4 different ways.
4 Techniques to Monitor Activity
Current DAM solutions are limited in their capacity to what they can do, leaving organizations struggling to build a tech stack sourcing from multiple solutions to manage a robust security posture.
Organizations can choose from 4 different monitoring techniques for their specific use-case—
1. Agentless Replication Logs
Change Data Capture (or CDC) can be used for near-realtime database backups, and are used for replication in a distributed system. CDC can be a preferred technique for monitoring activity as it doesn’t impact database operations and affect performance significantly.
For security posture it then needs to be ensured that the capturing of the changes for monitoring purposes is being performed without interruption. Any faults that interrupt these operations then can become potential attack vectors. Adaptive uses Stateless Capture Controllers (SCC) to ensure this doesn’t happen. Anytime the capture is interrupted, Adaptive smartly starts from the last known location on the table of operations native to the database. The CDC in Adaptive is, therefore, idempotent in nature.
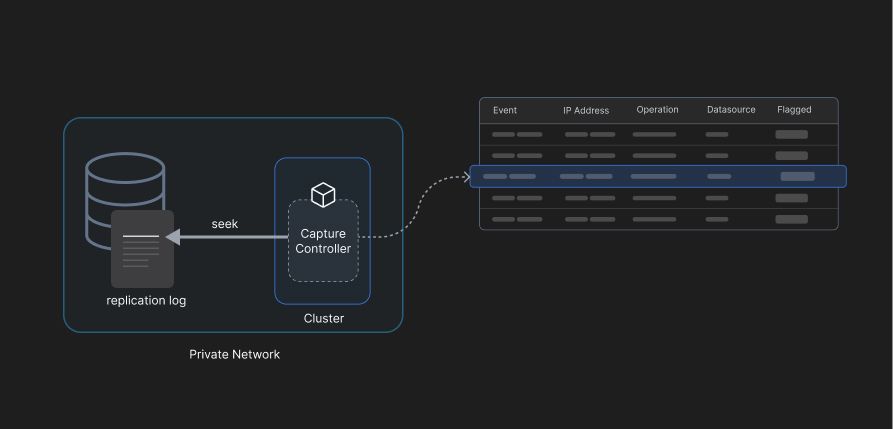
Although this is an effective method to capture malicious activity in the database through operations performed by end users, in case of an actual threat, tracking the event to the end user becomes difficult as the replication logs used by these capture controllers don’t track the user and meta information like IP-addresses, device used, etc. Incidence response than is left requiring assistance from other tools tracking access and privileges to the organizations’ resources.
2. Network-based Agents
One way to easily track IPs and track the device in case of a violation is to use Network Based Agents. Adaptive can capture and analyze network packets (known as Packet Sniffing) to detect and audit database activity. The agent can observe and intercept events for a given network interface, port, and protocol. Packets can be translated to database operations, mapped to policies creating an audit event when a violation is detected.
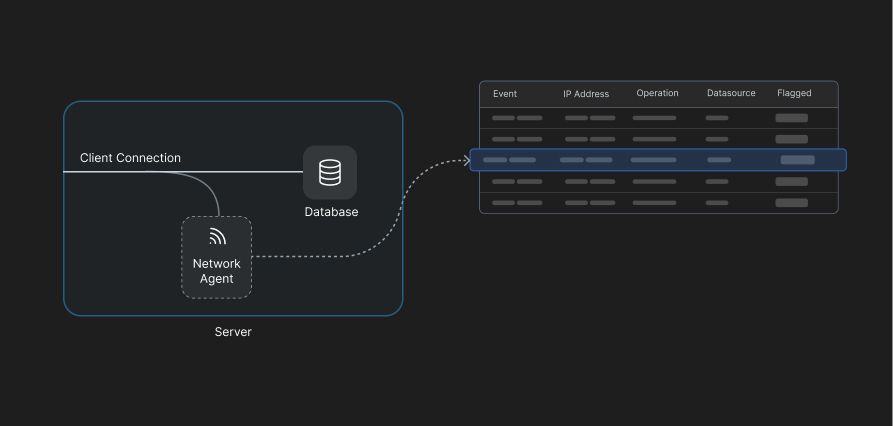
Packet sniffing is a powerful tool to monitor database activity and detect any data leakages by tracking the violating changes to the device, and eventually blocking access to contain the potential attack. However, in cases involving credential granted access, it isn’t enough to block device access but also to track the user and revoke any privileges.
3. Agentless Database Triggers
Unlike agents that are software scripts running separately in a database server, triggers are database objects embedded and running natively inside the database itself, allowing them to monitor malicious activities by intercepting the database operations like data manipulation language (DML) Events (e.g. insert, update, delete) or data definition language (DDL) events. Triggers are automatically created through policies, and effectively track states before and adter a change is made, along with the users creating them. The state tracking can be used to either PREVENT an operation, or DETECT a violation.
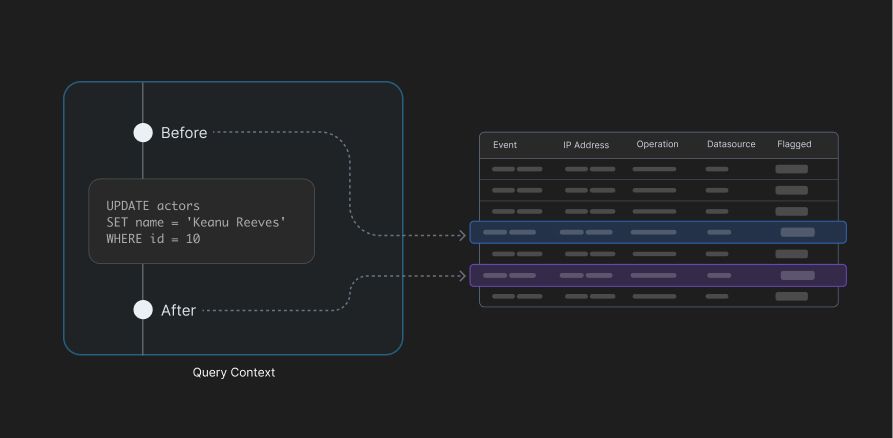
Adaptive, through the use of its Privilege Access Management (PAM) can easily track the database activity to the user and the device and be used to build response pipelines per violation.
4. Database General Logs
Need to be enabled at database initiation, each database tracks general logs (different from binary logs) which can then be used by Adaptive’s SCC to track malicious activity without fault.
Access Management and Monitoring with Adaptive
Adaptive discovers sensitive information, labels and classifies it into types for better security posture and then defines event policies that tracks all database activity for any potential violations leading to an improved security posture for the organization. Adaptive integrates with your choice of RDBMS—SQL and NoSQL—ranging from PostgreSQL and MySQL to MongoDB. All event logs, stored in CEF (Common Event Format) can be easily exported to Security Information and Event Management (SIEM) platform such as Splunk, SumoLogic, etc.
To effectively build remediation pipelines for incidence response, tracking activity to users and devices becomes important. Adaptive’s Privilege Access Management (PAM) solution therefore, using Principle of Least Privilege and Just-in-time Access, creates granular roles, reducing the attack surface. Not just that, it is a solution to credential sprawl, and helps with social phishing attacks. With Adaptive’s PAM, access can be as easily revoked as it can be granted giving admins and the security team a simple way to cut access and automate response pipelines.
 SOC2 Type II
SOC2 Type II