What is Sensitive Data and Why it needs to be Regulated?

Introduction
In 2022, 487 million WhatsApp users were put at risk, when a hacker posted their personal information online for public access. Later, Medibank, the Australian Healthcare Insurance provider suffered a critical data leak resulting in the theft of 9.7 million people’s information.
Over the past year, data breaches have accelerated by 10%, triggering an average hit of $9.48 million per data breach in the United States alone. Breaches and attacks leave the organization financially unstable, yes, but they also cause dents in reputation, stun operation for a while, and may cause major compliance penalties. Under all major cyberattacks, lies at risk and of great value; Sensitive Data.
What is Sensitive Data?
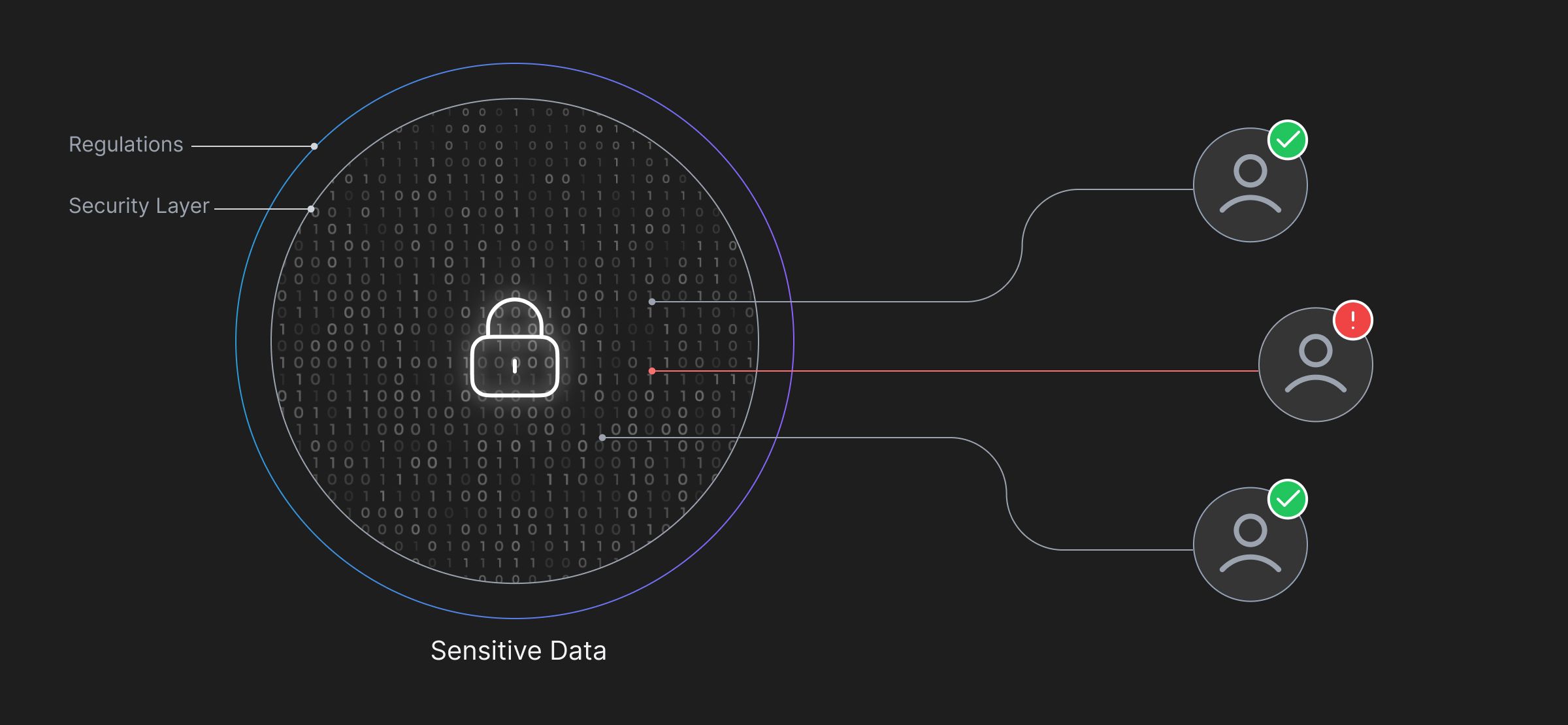
Sensitive Data is any information that must be protected from unauthorized access to safeguard an individual or an organization. It consists of any information that, if revealed, could cause negative effects such as violating someone's privacy, eroding trust in an organization, or illegally exploiting stakeholders' data.
While it comes in all shapes and sizes, most famously, sensitive data is used to identify individuals (PII), track health records (SPI), store extremely secret information by government organizations (Classified Information), etc. The ways it can be used for malicious intents are only limited by the attacker’s imagination.
Types of Sensitive Information
Sensitive information is ubiquitous, but also mostly private, i.e. not openly accessible through public networks. However, not all information is the same, e.g. health records might be more critical than personal identifying information, or, intellectual properties might be more important than a business’s financial records. In order to track, and in turn, regulate, the information needs to be categorized into silos. Following are the major information types that security engineers deal with, on a regular basis -
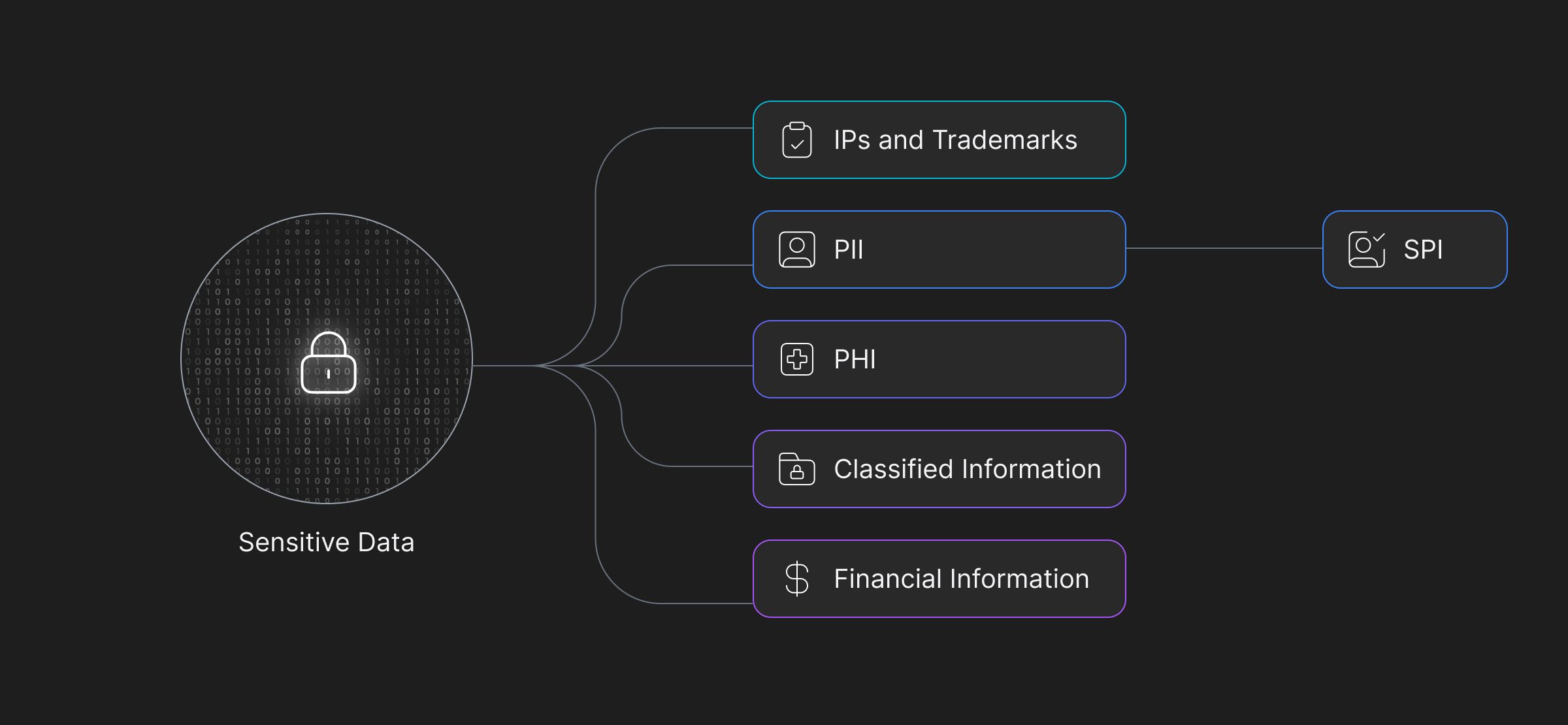
Personally Identifiable Information (PII)
Personally Identifiable Information is any detail that can lead to an individual such as social security numbers, full names, residential addresses, email addresses, and phone numbers, among others. Even today, PII theft remains an important challenge for organizations. Last year, Twitter (Now X.com) fell prey to a data breach exposing 200 million users’ identifying information (2022).
PII falls under a broader category of information; Personal Information (PI) which covers details like employment history, or financial information, and can directly or indirectly be linked to a person.
Sensitive Personal Information (SPI)
SPI is a subset of personal information that requires higher levels of protection due to its more vulnerable nature. If leaked, it can leave an individual vulnerable to discrimination or harassment. It can include details like race or ethnic origin, religion, and political affiliations among others.
Many regulations and compliance standards specifically outline rules for providing higher levels of security towards SPI.
Protected Health Information (PHI)
First defined under the privacy rule, a component of HIPPA, in 1996, PHI refers to any information about an individual's health status, provision of healthcare, or payment for healthcare that is created or collected by a Covered Entity (or a business associate of a Covered Entity) and which can be linked to a specific individual.
The definition contains 18 PHI identifiers, including unlikely details like IP addresses and vehicle identification numbers (VINs).
Classified information
Often tied to government or military organizations, classified information holds grave consequences when mishandled. These can compromise national security, confidential government communications, and other state secrets. Defense and Intelligence agencies take the utmost care to ensure this information is kept secure, but, it’s not bulletproof.
In 2013, Edward Snowden famously leaked intelligence documents showing the US government’s involvement in secretly monitoring and collecting citizen’s data. A little while back, in 2010, WikiLeaks published 100s of thousands of documents detailing war crimes that the US government had allowed to occur during the Iraq war.
Financial information
Financial records are undeniably crucial. From credit card numbers, bank account data, and transaction history to income details and financial forecasts of a business; its potential misuse can lead to financial fraud, insider trading, or severe disruption to an individual's or an organization's financial stability.
Intellectual Property (IP) and Trade Secrets
These are critical assets for many corporations. Including patents, software code, blueprints, strategies, and secret recipes among others, grant a company its competitive edge. Any unauthorized access or theft can result in significant financial losses and damage to their reputation.
Understanding different data types is paramount when creating systems for data protection or data privacy regulation compliance. Unregulated management of such data can lead to detrimental impacts for all parties involved. At best, it could lead to financial losses, at worst, it can compromise nuclear weapons.
Key Regulations and Compliance
Over the years, the need for protecting sensitive data has become increasingly evident. Increasing use of electronic records to store health information, businesses recording personal information, need to protect consumers’ financial information, all led to the establishment of various regulations and compliance standards.
The following regulations aim to safeguard individuals' privacy rights, prevent data breaches, and mitigate the potential risks associated with unauthorized access to sensitive information.
General Data Protection Regulation (GDPR)
Established by the EU in 2018, GDPR is a data privacy regulation that applies to organizations processing the personal data of EU citizens, no matter where the organization is located. GDPR requires firms to obtain explicit consent of the users to collect and process their information, while at all times the users retain rights to access, correct, and delete their records.
It has strict requirements, leading to heavy fines on non-compliance. Among other conditions, it requires the appointment of DPOs to process data in large amounts, conduct Data Protection Impact Assessments (DPIAs), and take sufficient technical measures to ensure safety. GDPR was a precursor to the creation of the California Consumer Privacy Act.
California Consumer Privacy Act (CCPA)
Also established in 2018, CCPA gives California residents increased control over how their data is processed and the right to access, correct, and delete these records.
Contrary to GDPR, CCPA only applies to for-profit organizations meeting certain revenue and data collection thresholds. CCPA requires adherence to standard requirements which makes it complex and requires ongoing effort to maintain compliance. The CCPA has been amended by the California Privacy Rights Act (CPRA), which expands certain consumer rights and creates a new state agency to enforce the law.
California Privacy Rights Act (CPRA)
A more recent consumer privacy act, amending and expanding CCPA, the CPRA applies to any and all data collected after 1 January 2022 and has been in effect since 1 January 2023.
Under personal information, CPRA adds and recognizes a new category of sensitive personal information including social security numbers, driver's license numbers, and biometric information. In addition to businesses with certain revenue and data collection thresholds, the CPRA also explicitly includes those that buy, sell, or share the personal information of 100,000 California consumers or households.
Health Insurance Portability and Accountability Act (HIPAA)
Established in 1996, HIPAA is a federal law, that defines standards for protecting patient’s health information. Applying to covered entities, including healthcare providers, health plans, and healthcare clearinghouses, and their business associates, HIPAA requires the protection of protected health information (PHI) and notifying individuals in the event of a breach.
Apart from granting control of their PHI, HIPPA also requires organizations to require explicit approval from individuals to use their PHI outside the confines of treatment, payment, or healthcare operations. Non-compliance can have serious fines, going up to $1.5 million per violation.
HIPPA’s detailed terms and conditions, like the 18 PHI identifiers, influenced regulations like GDPR.
Gramm-Leach-Bliley Act (GLBA)
Established in 1999, the GLBA is also a federal law, aimed at modernizing the financial services industry and protecting consumers’ financial data. It requests transparency in handling consumer data, and implementation of strict measures to protect sensitive customer information.
Applying to financial institutions offering consumers financial products or services like loans, financial or investment advice, or insurance, GLBA requires the complying institution to provide customers with a privacy notice explaining their information-sharing practices and gives customers the right to opt out of sharing.
Requiring implementation and maintenance of reasonable security measures to protect customer information, GLBA poses fines up to $100,000 per violation.
New York Stop Hacks and Improve Electronic Data Security (NY SHIELD) Act
Passed in 2019, the NY SHIELD Act is a data protection law, that amends New York's existing data breach notification law, imposing more Data Security requirements on companies collecting information from New York residents.
It applies to any person or business that owns or licenses private information of a NY resident, regardless of whether they conduct business in New York. It expands the definition of private information to include bio-metric information, username or email address in combination with a password or security questions and answers, and account numbers or credit card numbers that can be accessed without a security code, access code, or password.
NY SHIELD mandates companies to adopt administrative, technical, and physical safeguards to protect private information, fining up to $250,000 for any violations. It is complex and requires ongoing effort to maintain compliance.
Security by Compliance - What can you do for your organization?
In 2016, Banner Health System paid $1.25 million to settle the case of impermissibly disclosing the PHI of 2.8 million individuals owing to a data breach. Data Security is an easy answer but remains challenging to implement even for the most experienced professionals and organizations. Regulations ensure you are doing enough towards securing any critical data housed in your infrastructure.
Why should you choose to comply?
Understanding sensitive data is the initial step in building better security practices, but making data security and compliance an integral part of the company culture and daily operations involves establishing appropriate controls and policies, deploying the right tools and technologies, and training employees in good security practices and credential hygiene.
Data Regulations, in addition to being able to operate in an industry, offer a lot of benefits—
- Going the extra mile in securing certifications, builds trust in the organization.
- It attracts high-caliber talent, individuals who value working in a responsible and ethical environment.
- As data regulations continue to evolve and become more stringent, companies that are already compliant can maintain a competitive edge.
- By adhering to widespread regulations such as GDPR, companies can expand to broader markets with relative ease.
Maintaining Compliance with Adaptive
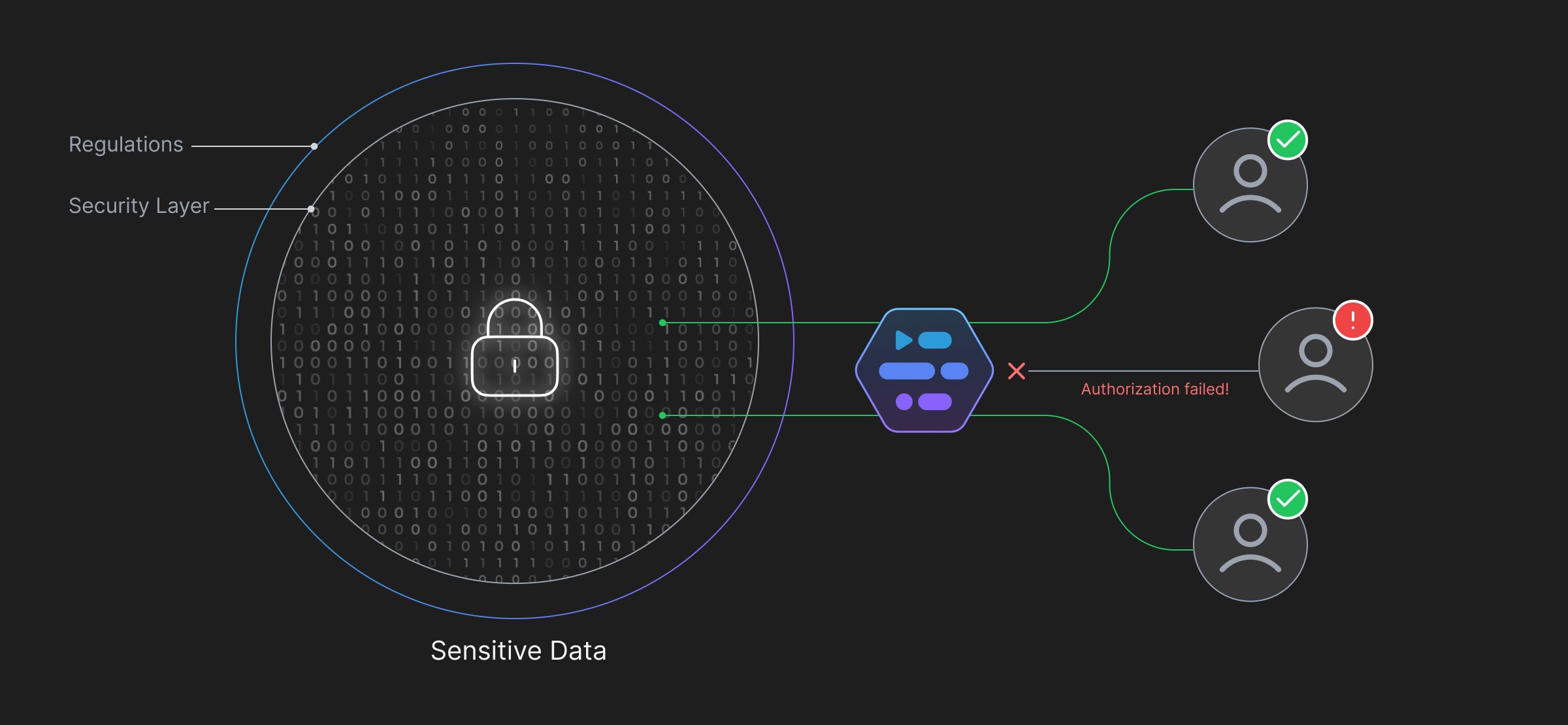 Adaptive offers Access Management and Data Security services for organizations handling critical data, and/or operating in heavily regulated industries. With Adaptive, you can—
Adaptive offers Access Management and Data Security services for organizations handling critical data, and/or operating in heavily regulated industries. With Adaptive, you can—
Discover Sensitive Data
Effortlessly create labels with priorities for Adaptive to automate datastore scanning and label any sensitive data to take proper security measures.
Define Rules to Protect Data
With Adaptive, you have the flexibility to create policies and rules around your labeled data to restrict modifications and access to how you want it to be. Policies can be defined to detect and prevent access to classified, confidential information.
Monitor Activity
Access and monitor user access and activity to ensure everything is as expected. The System identifies and authenticates the end-user's permissions, without which it restricts access.
Generate Compliance-Ready Reports
Generate compliance-ready reports such as access requests, user activities, and session recordings. Adaptive provides streamlined evidence gathering for SOC 2 and HIPAA compliance audits.
 SOC2 Type II
SOC2 Type II