Use Case
Protect Against Data Exfiltration
Adaptive monitors database activity, and detect any anomalous behaviour in real time. Deploy automated incident response pipelines to ensure your data remains with you.
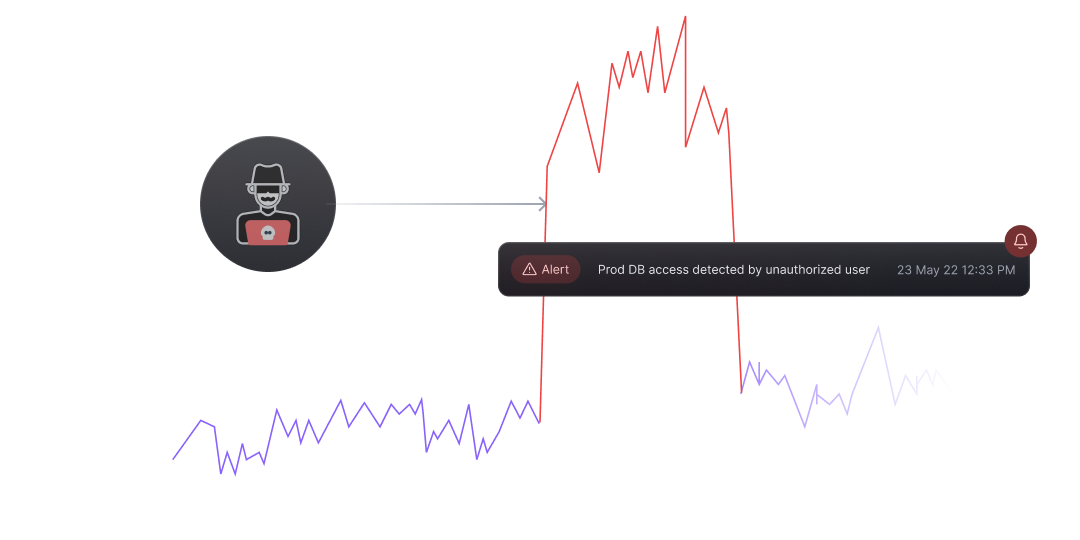

Data exfiltration is hard to detect. Attackers have come up with innovative ways to go undetected, like event based triggers on a privileged device, deploying malware on the resource to slowly transfer data, and brute force by copying data to an external device. Big exfiltration attempts happen over months, sometimes even years and are detected too late.
212 days
Average time to identify a data breach
75 days
Average time to contain a data breach
8.22 billion
Total records breached in 2023
Data exfiltration is a major concern for organizations, as it can lead to loss of sensitive data, intellectual property, and financial loss. It can also lead to loss of customer trust and reputation damage. Traditional security measures lack robust auditing and logging capabilities, leading to limited visibility into user activities, incomplete or inadequate logs, and lack of accountability.

Detect Anomalies and Deploy Response Pipelines for Automated Actions against threats
Adaptive monitors activity in real-time and deploys policies to detect violations. Through the integrated privilege access management (PAM), Adaptive tracks activity back to the user or device, and can help build automated response pipelines enabling security teams to block access in case of violations and take recuperating actions against the malicious user, such as, restricting further access, and alerting the security team. Adaptive tracks events and constantly trains it’s threat models to detect anomalous behaviour faster with time.
Real-time Monitoring
Real-time database activity monitoring across infrastructure resources to detect policy violations and restrict access to check threats.
Policies deployed against labelled data protect it from any unusual access activity, like DDL operations.
Better security with time
Adaptive’s threat and anomaly detection models constantly monitor activity against benchmarks and previous threats. Any new verified threat is also added to the arsenal for strengthened protection.
Anomaly detection models can effectively detect slow and irregular data bleeding patterns, alerting security teams promptly.
Anomaly Detection
Get alerted as irregularities and anomalous patterns are detected.
Adaptive tracks and maps access patterns in real time and deploys policies for violation detection. Alerts and response pipelines can be built over it.
Enterprise Grade
Protect Against Data Exfiltration
Agentless Architecture
Zero Network Reconfiguration
Deploy in Cloud or On-Prem

Comprehensive Data Security Stack for Regulated Industries
 SOC2 Type II
SOC2 Type IIProduct
Use Cases
Industries